Claims administration and risk management company Sedgwick has confirmed that its federal contractor subsidiary, Sedgwick Government Solutions, was the victim of a security breach.
Sedgwick also employs over 33,000 people and serves 10,000 clients across 80 countries, including 59% of the Fortune 500, and its subsidiary serves over 20+ government agency clients.
The list of federal agencies using Sedgwick Government Solutions’s services includes the Cybersecurity and Infrastructure Security Agency (CISA), the Department of Commerce, the United States Citizenship and Immigration Services (USCIS), the United States Coast Guard, the Department of Homeland Security (DHS), the U.S. Department of Labor, the Customs and Border Protection (CBP), and the U.S. Coast Guard.

A Sedgwick spokesperson told BleepingComputer that the company is currently investigating a security breach that impacted its subsidiary, adding that the parent company’s network was not affected.
Sedgwick has also notified law enforcement and has hired outside cybersecurity experts to investigate the impact of the breach.
“Sedgwick is addressing a security incident at one of its subsidiaries, Sedgwick Government Solutions. Following the detection of the incident, we initiated our incident response protocols and engaged external cybersecurity experts through outside counsel to assist with our investigation of the affected isolated file transfer system,” the spokesperson said.
“Importantly, Sedgwick Government Solutions is segmented from the rest of our business, and no wider Sedgwick systems or data were affected. Further, there is no evidence of access to claims management servers nor any impact on Sedgwick Government Solutions ability to continue serving its clients. We have notified law enforcement and remain in contact with our clients as we conduct our investigation.”
While the company didn’t attribute the attack to a specific threat group, the statement confirms the TridentLocker ransomware group’s claims that they breached the company.
The threat actors say they’ve stolen 3.39 GB of documents and, since taking responsibility for the attack, they’ve also published some of the allegedly stolen data on their Tor data leak website.
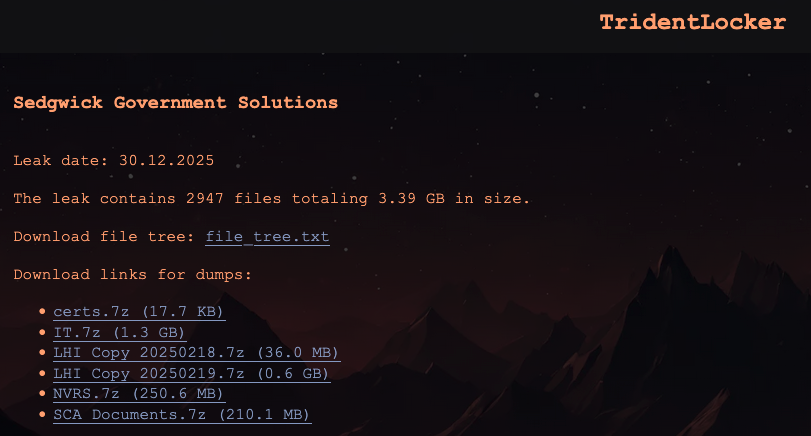
TridentLocker ransomware first surfaced in November and is currently listing a dozen victims on its leak site, including Bpost (Belgian Post Group), the company that delivers mail in Belgium and one of the largest civilian employers in the country.
Bpost confirmed its network was breached on December 3rd but said its operations were not affected by the TridentLocker ransomware attack.

It’s budget season! Over 300 CISOs and security leaders have shared how they’re planning, spending, and prioritizing for the year ahead. This report compiles their insights, allowing readers to benchmark strategies, identify emerging trends, and compare their priorities as they head into 2026.
Learn how top leaders are turning investment into measurable impact.
