Iron Mountain, a leading data storage and recovery services company, says that a recent breach claimed by the Everest extortion gang is limited to mostly marketing materials.
Headquartered in Portsmouth, New Hampshire, and founded in 1951, Iron Mountain specializes in data centers and records management, and has over 240,000 customers worldwide from more than 61 countries, including 95% of the Fortune 1000.
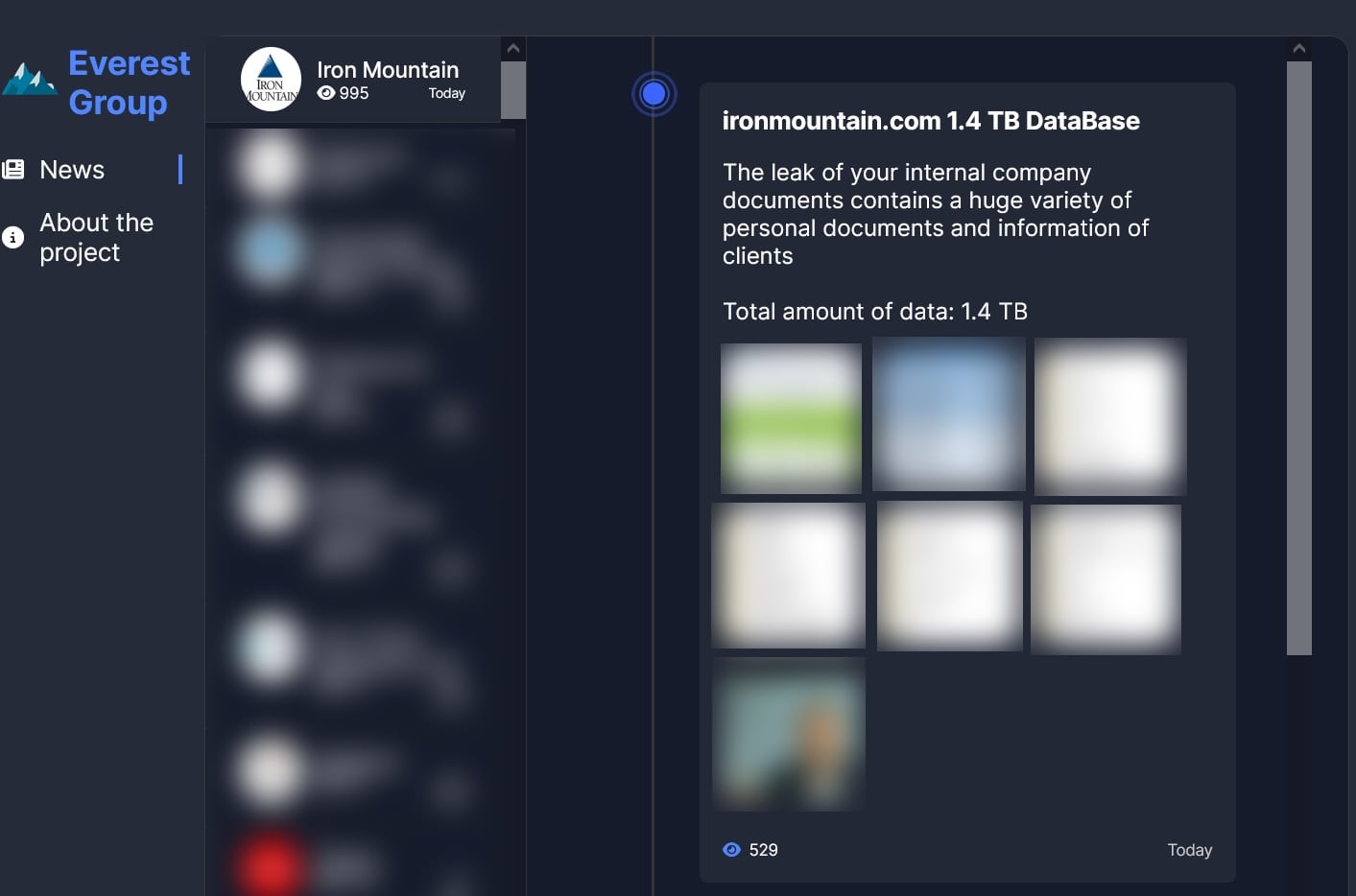
The company’s statement comes after the cybercrime group claimed on its dark web leak site that it had stolen 1.4 TB of “internal company documents” containing “personal documents and information on clients.”

However, Iron Mountain told BleepingComputer that the attackers used compromised credentials to access a single folder on a file-sharing server storing marketing materials.
It also added that the Everest operators didn’t deploy any ransomware payloads on the server, and no other Iron Mountain systems were breached in the incident.
“No customer confidential or sensitive information has been involved. A single compromised login credential was used to gain access to one folder, consisting primarily of marketing materials shared with third-party vendors on a public-facing file-sharing site,” the company told BleepingComputer.
“At this time, we also confirm that no Iron Mountain systems have been breached, and there is no ransomware or malware involvement, or any other cyber activity, beyond the compromised folder credential, which has since been deactivated.”
Since it surfaced in 2020, the Everest ransomware group has shifted tactics from encrypting victims’ systems with ransomware to data-theft-only corporate extortion.
Everest is also known for acting as an initial access broker for other threat actors and cybercrime gangs, selling access to breached corporate networks for a fee.
Over the last 5 years, Everest has added hundreds of victims to its leak portal, which is used in double-extortion attacks in which the threat actors threaten to publish stolen files unless victims pay ransoms.
In August 2024, the U.S. Department of Health and Human Services also warned that Everest was increasingly targeting healthcare organizations across the United States.
More recently, the cybercrime operation took down its website in April 2025 after it was defaced and its contents replaced with the “Don’t do crime CRIME IS BAD xoxo from Prague” message.

Modern IT infrastructure moves faster than manual workflows can handle.
In this new Tines guide, learn how your team can reduce hidden manual delays, improve reliability through automated response, and build and scale intelligent workflows on top of tools you already use.
