Table of Contents
23 Apr 2025
•
,
5 min. read

When Google enters a particular market, it often means bad news for the incumbents. So it was with Google Forms, the tech giant’s form and quiz-building tool that launched in 2008. According to one estimate, it now has a market share of nearly 50%.
However, with great market share comes greater scrutiny from nefarious elements. Threat actors are past masters at abusing popular technology for their own ends. And they are doing so with Google Forms to harvest sensitive information from their victims and even trick them into installing malware.
Why Google Forms?
Malicious actors are always looking for ways to add legitimacy to scams and evade email security filters. Google Forms offers a great opportunity to do both. It is favored by cybercriminals because it is:
- Free, meaning threat actors can launch campaigns at scale with a potentially lucrative return on their investment
- Trusted by users, which increases the chances of victims believing that the Google Form they’re being sent or redirected to is legitimate
- A legitimate service, meaning that malicious Google Forms and links to malicious forms are often waved through by traditional email security tools
- Easy to use, which is good for users but also handy for cybercriminals – meaning they can launch convincing phishing campaigns with very little effort or prior knowledge of the tool
- Cybercriminals also take advantage of the fact that Google Forms communications are encrypted with TLS, which may make it harder for security tools to peer in and check for any malicious activity. Similarly, the solution often uses dynamic URLs, which may make it challenging for some email security filters to spot malicious forms.
What do Google Forms attacks look like?
Most Google Forms threats use the tool to trick users into handing over their personal and financial information, although there are slight variations on how threat actors achieve this. Here are some of the main techniques to look out for:
Threat actors create Google Forms designed to spoof legitimate brands, such as log-in pages for social media sites, banks and universities, or even payment pages. As mentioned, the advantage for the bad guys is that it’s quicker, easier and cheaper to do so than build a dedicated phishing site, and less likely to be blocked by security filters.
Typically, you will receive a link to one of these malicious Google Forms via a phishing email, which itself may be spoofed to impersonate a legitimate brand or sender. The email may even come from a legitimate account that has been hijacked. Either way, the end goal is usually to:
- Harvest your log-ins, which can then be used to hijack accounts and commit identity fraud
- Steal your card details or banking/crypto information in order to take over these accounts and drain them of funds or commit payment fraud
- Persuade you to click on a link in the malicious Google Form that redirects you to a site which covertly installs malware on your machine
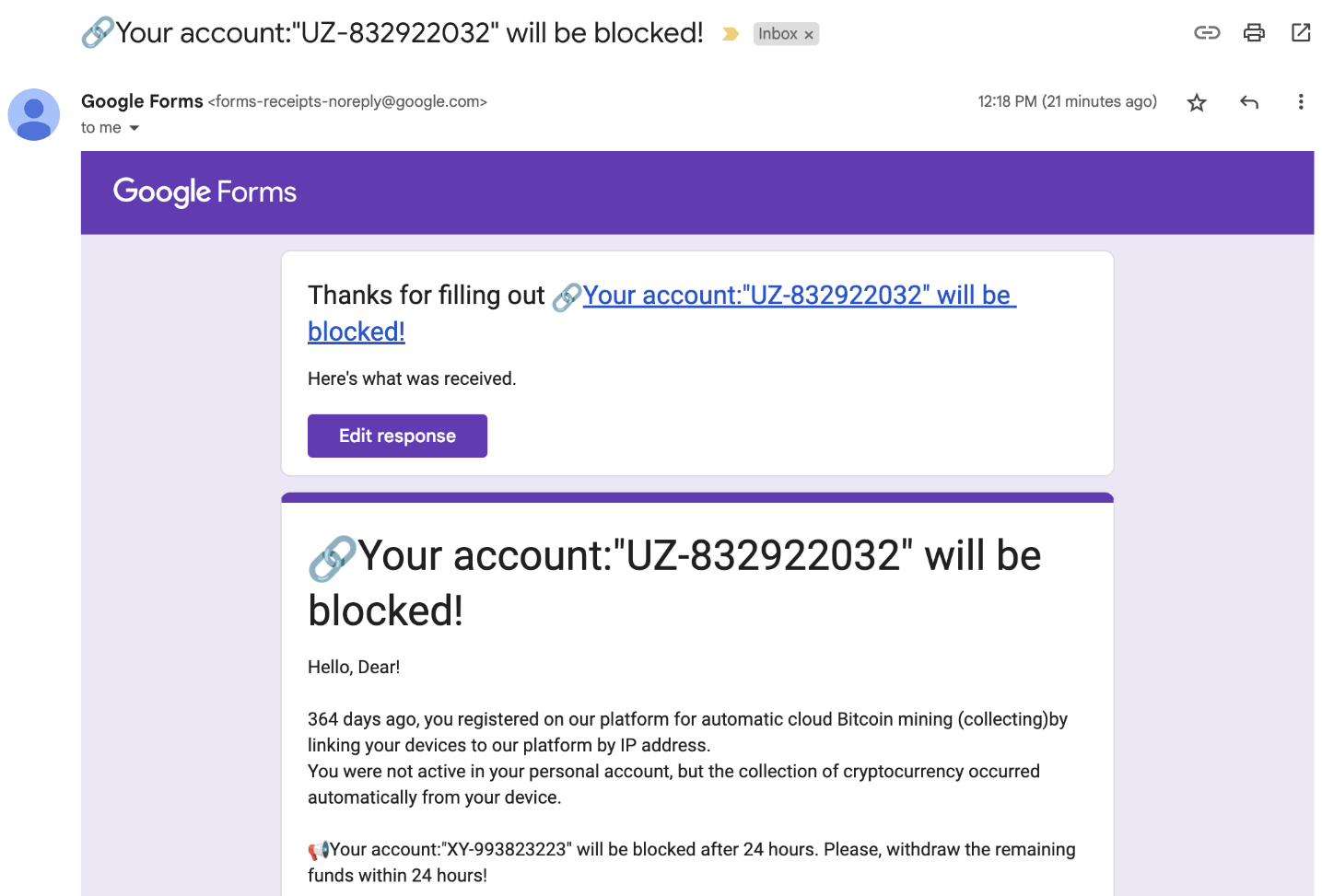
Call back phishing
Attackers send you a malicious Google Form crafted to trick you into calling a phone number listed on it. The form may be spoofed to appear as if sent from a bank or other trusted service provider. A sense of urgency is created to rush you into making a rash decision – calling the number without thinking things through first. Often the form will state that your account will be blocked or that money was taken (or will be taken from your account) unless you get in touch.
Once you call back, you’ll be speaking to a member of a voice phishing (vishing) gang that uses charm to convince you into handing over personal and financial information. They may also suggest downloading remote access software to your machine, which would give them full control over your computer.
Quiz spam
Cybercriminals might abuse the quiz feature in Google Forms – by creating a quiz and adding your email address. Hitting “release scores” will generate a message which the threat actor can customize – possibly adding links to phishing, malware or scam sites.
Attacks in the wild
Among the real-world campaigns security researchers have seen in recent years are:
BazarCall
A vishing-type threat in which victims received an email containing a malicious Google Form impersonating PayPal, Netflix, or one of several other big-name brands. The form contained details of a fake charge which is about to be applied, unless the recipient calls the phone number supplied.
Phishing targeting US universities
Google detected an increase in attacks on the US education sector last year. Victims received phishing emails containing a link to a malicious Google Form. Both the initial email and form were spoofed to appear as if sent by the university, by featuring logos, mascots and references to the university name. The end goal was to harvest logins and/or financial details.
Keeping your defenses up
Awareness is half the battle when it comes to mitigating the impact of social engineering threats like this. Now that you know how the bad guys operate, it should be harder for them to trick you into making bad choices online. To keep Google Form threats at bay, consider the following:
- Use multi-layered security software from a reputable provider on all computers and mobile devices. This will help to ensure that, even if you click on a malicious link, the malware download will be blocked. Good software will also spot suspicious patterns, even if the Google Form itself appears legitimate, as well as scan your machine/device periodically and keep you safe from anything malicious.
- Stay alert to potential phishing scams. You shouldn’t trust anything unsolicited which asks you to click on a link or call a number urgently. Instead, take a deep breath, relax, and contact the sender separately; not via the number or link provided. Another useful tactic is to hover over links to check the real destination. Make sure your email security solution
- Enhance security at log-in by using strong, unique passwords for every account, stored in a password manager for easy recall. Then switch on multi-factor authentication (MFA) for every account you use online. This means that, even if hackers get hold of your password, they can’t access your account. A hardware-based security key or an authenticator app is best.
- Pay attention: Google always displays a warning on Google Forms, telling recipients “Never submit passwords through Google Forms”. Follow its advice.
If the worst happens and you think you’ve fallen victim to a Google Forms attack, change your passwords, run a malware scan, and tell your bank to freeze any cards (if you’ve submitted card details). Switch on MFA for all accounts if you’ve not already, and monitor your accounts for any unusual activity.
Simply by reading this article, you will be in a good place when it comes to fending off the threat from malicious Google Forms. Be skeptical of any unsolicited email you receive – even if it’s from a trusted brand.
