Table of Contents
In January 2024, Russian hackers broke into Microsoft’s systems by slipping past what many believed was an ironclad security setup. The attack proved that even with multiple layers of protection, passwords often remain the weakest link in network security.
It was a stark reminder for IT teams that no matter how sophisticated our security tools become; the humble password still matters… a lot.
Common password vulnerabilities that undermine security
Despite all the advanced authentication technologies, passwords continue to be the primary way attackers move through corporate networks. That makes it more important than ever to ensure your organization employs robust password controls.
Today’s IT environments are a tangled web of systems that defy simple security solutions. On-premises servers, cloud platforms, and remote work setups each add another layer of complexity to password management.
It’s like trying to secure a house with multiple entrances, each with a unique lock and a different set of keys.
Where password controls break down
Forgotten accounts and legacy systems
Legacy accounts are like forgotten spare keys hidden under old doormats, just waiting for someone to find them. Windows Active Directory domains, standalone systems, and specialized application accounts have become the digital equivalent of unlocked side doors that nobody remembers to check. These forgotten entry points are a hacker’s dream, offering easy access to networks that think they’re buttoned up tight.
User fatigue and predictable patterns
Before you start pointing fingers at users, consider their reality: the average person struggles to keep track of up to 170 passwords. They’ve learned to game the system with pedictable quick tricks: adding a number, swapping an ‘a’ for an ‘@’, or tossing in an exclamation point.
These passwords may look tough, but they’re about as secure as a paper lock. And hackers? They love this setup. It’s like finding a master key that opens multiple buildings, with each leaked password potentially unlocking an entire corporate network.
Verizon’s Data Breach Investigation Report found stolen credentials are involved in 44.7% of breaches.
Effortlessly secure Active Directory with compliant password policies, blocking 4+ billion compromised passwords, boosting security, and slashing support hassles!
Try it for free
Practical controls for stronger password security
Forget checkbox security. Protecting passwords isn’t about ticking boxes; it’s about building a smart, adaptive strategy. Your organization must move past simple complexity requirements to implement intelligent, dynamic password management strategies.
Smarter password lists and detection
This means creating banned password lists that are far more sophisticated than basic dictionary checks. These lists should include leaked passwords, company-specific variations, and advanced pattern recognition that identifies subtle security risks.
Intelligent password history and rotation
Traditional rotation policies often backfire, pushing users to make predictable changes like adding a number or changing a character. Instead, deploy nuanced rotation strategies that prevent password recycling while avoiding user frustration.
The goal is to create a rotation strategy that throws attackers off their game without driving users crazy.
Prioritize length and memorability
For the greatest level of password security, remember: length and memorability beat complexity every time. A long passphrase that means something to the user is infinitely stronger than a short, cryptic password that requires a flowchart to remember.
It’s about working with human nature, not fighting against it.
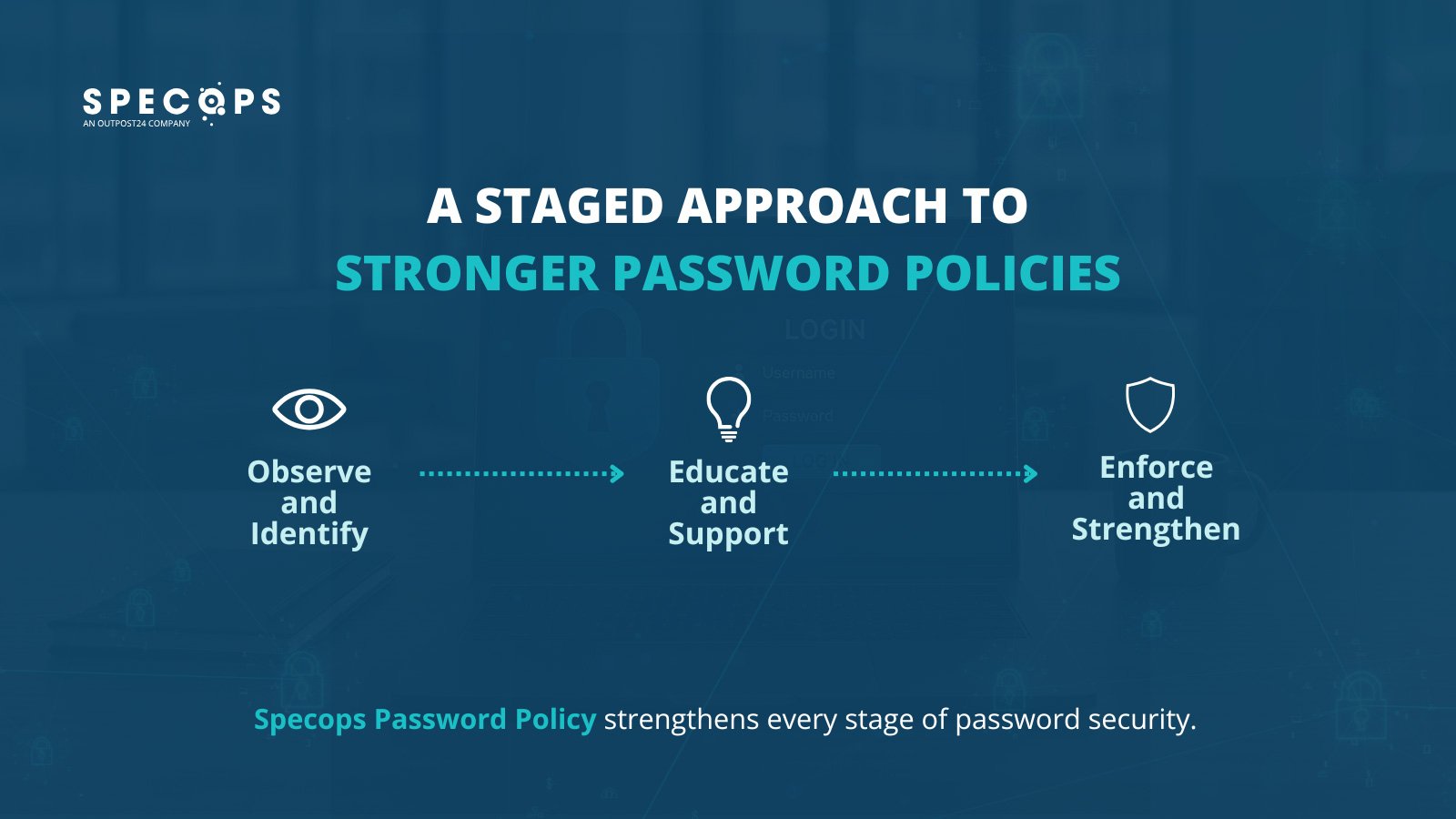
A staged approach to enforcing password policies
Implementing password policies is part security strategy, part psychology. Start by watching and learning, collecting data on how people actually use passwords. Then, give gentle nudges about potential weaknesses.
Finally, start implementing mandatory changes with clear, supportive guidance; it’s important that users don’t feel like they’re being punished.
Password security playbook: From audit to implementation
Securing passwords starts with an audit of your most critical access points. Privileged accounts, admin, service, and high-access logins, need maximum protection. These are your network’s most valuable targets, and attackers know it. Multi-factor authentication isn’t just about compliance; it’s your last defense against sophisticated breaches.
Self-service password resets should be a balance between user-friendly and rock-solid security. The goal is a system that is so intuitive that users don’t get frustrated, and so intelligent that attackers can’t find a way in.
Risk-based authentication takes this a step further, dynamically assessing each password change request based on context like device, location, and user behavior. It’s like having a digital bouncer that knows exactly who should and shouldn’t get past the velvet rope.
Measuring the success of your password security strategy
The right metrics reveal where your vulnerabilities hide and how effectively you’re closing those gaps. To get a clear picture of your password security health, focus on KPIs like:
- Percentage of banned passwords caught and removed
- Reduction in help desk password reset tickets
- Decrease in time required to remediate potential vulnerabilities
Then, put those metrics into action, focusing your efforts on a plan that moves you from password panic to real protection.
A 90-day plan to strengthen password security
First 30 days: Deep dive and discovery. Conduct a complete reconnaissance of your password landscape, mapping out every system, identifying every account type, and understanding how passwords are currently being used (and abused). Run password vulnerability scans and analyze password complexity across your organization to create a baseline that shows where you stand.
Next 60 days: Strategic implementation. With your baseline established, it’s time for a smart, staged implementation. Start with pilot groups in less sensitive departments to test your new password strategies:
- Develop training that goes beyond “use a complex password”
- Educate teams on the real-world implications of password vulnerabilities
- Roll out new policies incrementally, with clear communication and support
By the end of this journey, you’ll have transformed your password strategy, creating adaptive, intelligent protection that evolves with your organization.
Password security still matters
Passwords aren’t going anywhere. They remain the fallback for even the most advanced authentication methods. By implementing intelligent, dynamic password controls, your organization can turn them from a constant security challenge into a resilient defense mechanism. The key lies in understanding that password security is not a one-time fix but an ongoing, ever-changing strategy.
Ready to turn password security from a constant headache into a strategic defense? Specops Password Policy makes it simple to build an effective password policy, plus it automatically scans your Active Directory against over 4 billion known unique compromised passwords.
Book a live demo today.
Sponsored and written by Specops Software.
