Table of Contents
Multiple current and former Target employees have reached out to BleepingComputer to confirm that the source code and documentation shared by a threat actor online match real internal systems.
A current employee also shared internal communications announcing an “accelerated” security change that restricted access to Target’s Enterprise Git server, rolled out a day after BleepingComputer first contacted the company about the alleged leak.
Employees verify authenticity of leaked materials
Yesterday, BleepingComputer exclusively reported that hackers are claiming to be selling Target’s internal source code after publishing what appears to be a sample of stolen repositories on Gitea, a public software development platform.

Since then, multiple sources with direct knowledge of Target’s internal CI/CD pipelines and infrastructure have reached out with information corroborating the authenticity of the leaked data.
A former Target employee confirmed that internal system names seen in the sample, such as “BigRED” and “TAP [Provisioning],” correspond to real platforms used at the company for cloud and on-premise application deployment and orchestration.
Both a current and the former Target employee also confirmed that elements of the technology stack, including Hadoop datasets, referenced in the leaked sample align with systems used internally.
This includes tooling built around a customized CI/CD platform based on Vela—a fact Target has also previously mentioned publicly, as well as the use of supply-chain infrastructure such as JFrog Artifactory, as also evident from third-party business intel.
The employees also independently referenced proprietary project codenames and taxonomy identifiers, such as those known internally as “blossom IDs,” that appear in the leaked dataset.
The presence of these system references, employee names, project names, and matching URLs in the sample further supports that the material reflects a real internal development environment rather than fabricated or generic code.
If you are a Target employee or have any information with regards to this event, confidentially send us a tip online or via Signal at @axsharma.01.
Target rolls out ‘accelerated’ access change
A current employee, who requested anonymity, also shared a screenshot of a company-wide Slack message in which a senior product manager announced a rapid security change, a day after BleepingComputer had contacted Target:
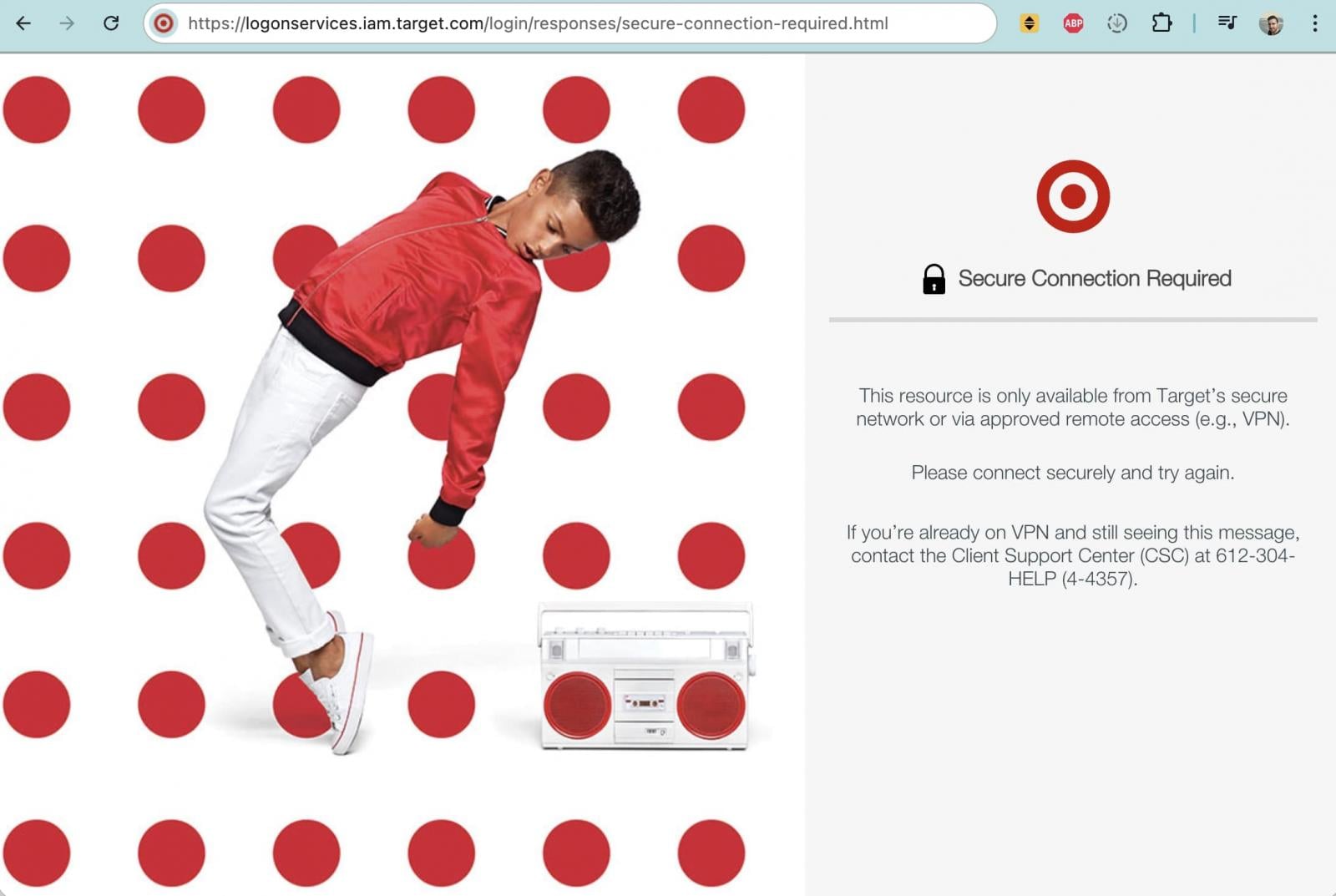
“Effective January 9th, 2026, access to git.target.com (Target’s on-prem GitHub Enterprise Server) now requires connection to a Target-managed network (either on-site or via VPN). This change was accelerated and aligns with how we’re handling access to GitHub.com,” the manager is seen stating.
Enterprise Git servers can host both private repositories, visible only to authenticated employees, and public open-source projects.
At Target, however, open-source code is generally hosted on GitHub.com, while git.target.com is used for internal development and requires employee authentication.
As reported yesterday, git.target.com was accessible over the web until last week and prompted employees to log in. It is now no longer reachable from the public internet and can only be accessed from Target’s internal network or corporate VPN, indicating a lockdown of access to the company’s proprietary source code environment.
Data leak, breach or insider involvement?
The root cause of how the data ended up in the hands of the threat actor has not yet been determined.
However, security researcher Alon Gal, CTO and co-founder of Hudson Rock, told BleepingComputer that his team has identified a Target employee workstation that was compromised by infostealer malware in late September 2025 and had extensive access to internal services.
“There is a recently infected computer of a Target employee with access to IAM, Confluence, wiki, and Jira,” Gal told BleepingComputer.
“It’s especially relevant because, despite tens of infected Target employees we’ve seen, almost none had IAM credentials and none had wiki access, except for one other case.”
There is no confirmation that this infection is directly connected to the source code now being advertised for sale. However, it is not uncommon for threat actors to exfiltrate data and only attempt to monetize or leak it months later. For example, the Clop ransomware gang began extorting victims through data leak threats in October 2025 for materials stolen as early as July that year.
The threat actor claims the full dataset is approximately 860GB in size. While BleepingComputer has only reviewed a 14MB sample comprising five partial repositories, employees say even this limited subset contains authentic internal code and system references, raising questions about the scope and sensitivity of what the much larger archive could contain.
BleepingComputer shared the Gitea repository links with Target last week and later offered to pass along Hudson Rock’s threat-intelligence findings to aid with investigation. The company has not responded to follow-up questions and remains silent on whether it is investigating a breach or potential insider involvement.

Whether you’re cleaning up old keys or setting guardrails for AI-generated code, this guide helps your team build securely from the start.
Get the cheat sheet and take the guesswork out of secrets management.
