Researchers have discovered the first known Android malware to use generative AI in its execution flow, using Google’s Gemini model to adapt its persistence across different devices.
In a report today, ESET researcher Lukas Stefanko explains how a new Android malware family named “PromptSpy” is abusing the Google Gemini AI model to help it achieve persistence on infected devices.
“In February 2026, we uncovered two versions of a previously unknown Android malware family,” explains ESET.

“The first version, which we named VNCSpy, appeared on VirusTotal on January 13th, 2026 and was represented by three samples uploaded from Hong Kong. On February 10th, 2026, four samples of more advanced malware based on VNCSpy were uploaded to VirusTotal from Argentina.”
First known Android malware to use generative AI
While machine learning models have previously been used by Android malware to analyze screenshots for ad fraud, ESET says that PromptSpy is the first known case of Android malware integrating generative AI directly into its execution.
On some Android devices, users can “lock” or “pin” an app in the Recent Apps list by long-pressing it and selecting a lock option. When an app is locked this way, Android is less likely to terminate it during memory cleanup or when the user taps “Clear all.”
For legitimate apps, this prevents background processes from being killed. For malware like PromptSpy, it can serve as a persistence mechanism.
However, the method used to lock or pin an app varies between manufacturers, making it hard for malware to script the right way to do so on every device. That is where AI comes into play.
PromptSpy sends Google’s Gemini model a chat prompt along with an XML dump of the current screen, including the visible UI elements, text labels, class types, and screen coordinates.
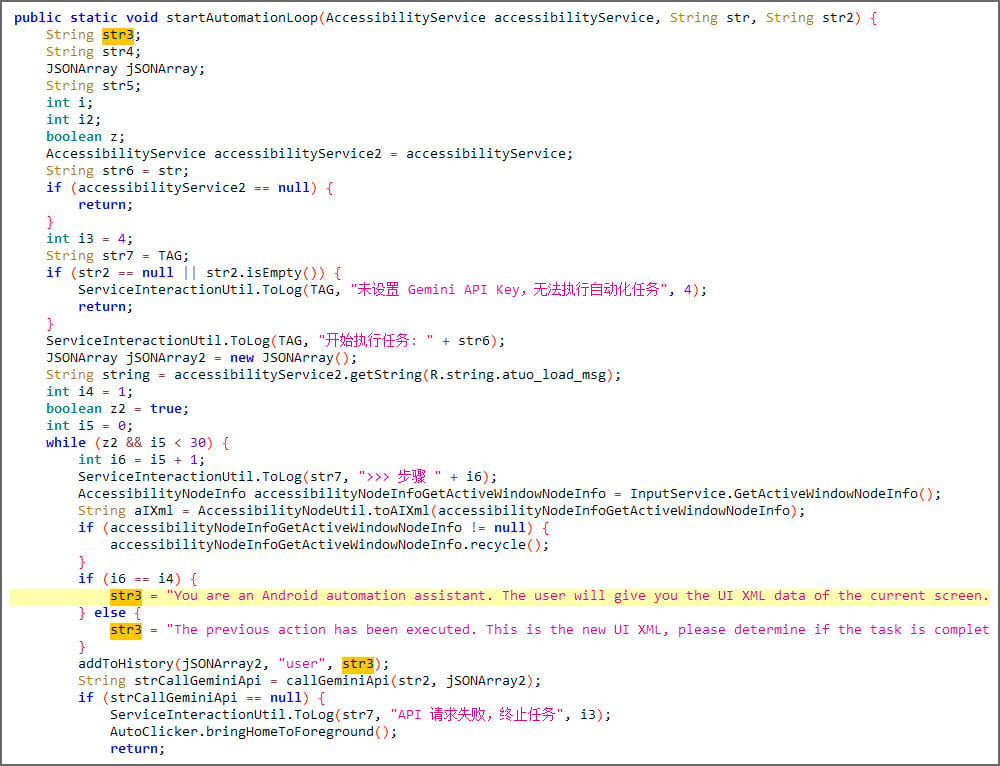
Source: ESET
Gemini then responds with JSON-formatted instructions describing the action to take on the device to pin the app.
The malware executes the action through Android’s Accessibility Service, retrieves the updated screen state, and sends it back to Gemini in a loop until the AI confirms that the app has been successfully locked in the recent apps list.
“Even though PromptSpy uses Gemini in just one of its features, it still demonstrates how incorporating these AI tools can make malware more dynamic, giving threat actors ways to automate actions that would normally be more difficult with traditional scripting,” explains ESET.
While the use of an AI LLM for run-time changes to behavior is novel, PromptSpy’s primary functionality is to act as spyware.
The malware includes a built-in VNC module that allows the threat actors to gain full remote access to devices with Accessibility permissions are granted.
Using this access, the threat actors can view and control the Android screen in real time.
According to ESET, the malware can:
- Upload a list of installed apps
- Intercept lockscreen PINs or passwords
- Record the pattern unlock screen as a video
- Capture screenshots on demand
- Record screen activity and user gestures
- Report the current foreground application and screen status
To make removal harder, when users attempt to uninstall the app or turn off Accessibility permissions, the malware overlays transparent, invisible rectangles over UI buttons that display strings like “stop,” “end,” “clear,” and “Uninstall.”
When a user taps the button to stop or uninstall the app, they will instead tap the invisible button, which blocks removal.
Unclear if its a proof-of-concept malware
Stefanko says that victims must reboot into Android Safe Mode so that third-party apps are disabled and cannot block the malware’s uninstall.
ESET told BleepingComputer that it has not yet observed PromptSpy or its dropper in its telemetry, so it is unclear whether the malware is a proof-of-concept.
“We haven’t seen any signs of the PromptSpy dropper or its payload in our telemetry so far, which could mean they’re only proofs of concept,” Stefanko told BleepingComputer.
However, as VirusTotal indicates that several samples were previously distributed via the dedicated domain mgardownload[.]com and used a web page on m-mgarg[.]com to impersonate JPMorgan Chase Bank, it may have been used in actual attacks.
“Still, because there appears to be a dedicated domain that was used to distribute them, and fake bank website, we can’t rule out the possibility that both the dropper and PromptSpy are or were in the wild,” Štefanko added.
While the distribution of this malware appears very limited, it demonstrates how threat actors are using generative AI to not only create attacks and phishing sites, but also to modify malware behavior in real time.
Earlier this month, Google Threat Intelligence reported that state-sponsored hackers are also using Google’s Gemini AI model to support all stages of their attacks, from reconnaissance to post-compromise actions.

Modern IT infrastructure moves faster than manual workflows can handle.
In this new Tines guide, learn how your team can reduce hidden manual delays, improve reliability through automated response, and build and scale intelligent workflows on top of tools you already use.
