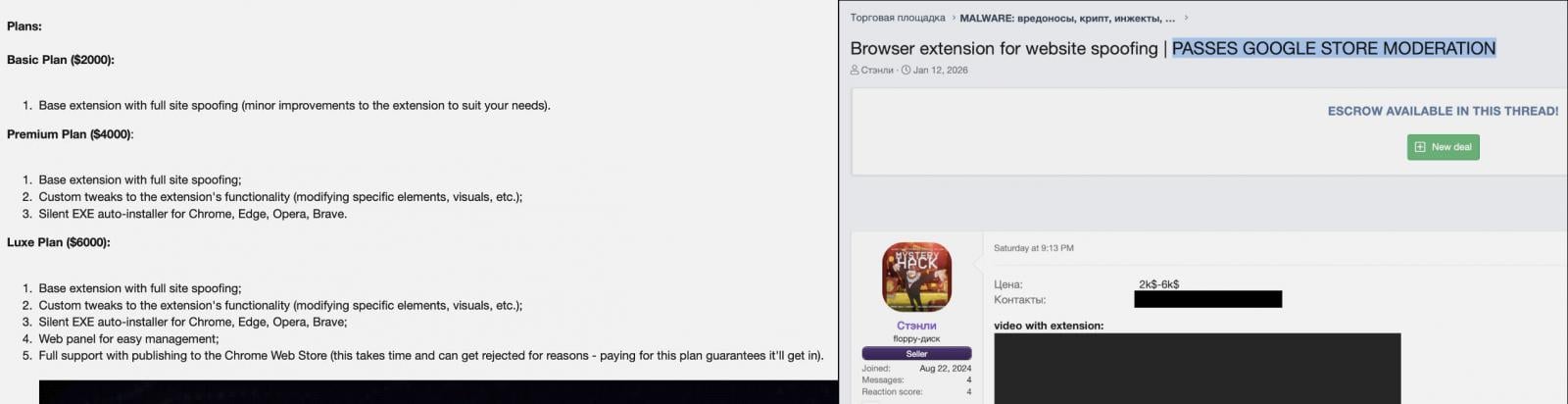
A new malware-as-a-service (MaaS) called ‘Stanley’ promises malicious Chrome extensions that can clear Google’s review process and publish them to the Chrome Web Store.
Researchers at end-to-end data security company Varonis named the project Stanley after the alias of the seller, who advertises easy phishing attacks by intercepting navigation and covering a webpage with an iframe with content of the attacker’s choice.
The new MaaS offering is for malicious Chrome extensions that can cover a webpage with a full-screen iframe containing phishing content of the attacker’s choice. Stanley also advertises silent auto-installation on Chrome, Edge, and Brave browsers and support for custom tweaks.

The MaaS has multiple subscription tiers, the most expensive one being the Luxe Plan, which also offers a web panel and full support for publishing the malicious extension to the Chrome Web Store.
Source: Varonis
BleepingComputer has contacted Google to request a comment on those claims, and we will update this post when we hear back.
Varonis reports that Stanley works by overlaying a full-screen iframe with malicious content while the victim’s browser address bar remains untouched, showing the legitimate domain.
.jpg)
Source: Varonis
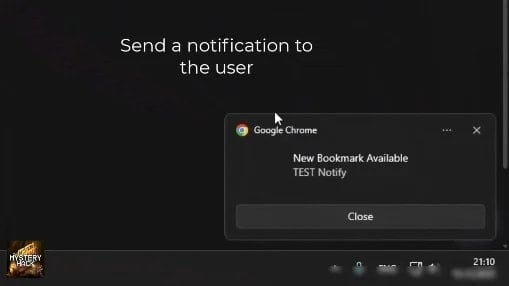
Operators who have access to Stanley’s panel can enable or disable hijacking rules on demand, or even push notifications directly in the victim’s browser to lure them to specific pages, pushing the phishing process more aggressively.
Source: Varonis
Stanley supports IP-based victim identification and enables geographic targeting and correlation across sessions and devices.
Moreover, the malicious extension performs persistent command-and-control (C2) polling every 10 seconds, and it can also perform backup domain rotation to provide resilience against takedowns.
Varonis comments that, from a technical perspective, Stanley lacks advanced features and instead opts for a straightforward approach to implementing well-known techniques.
Its code is reportedly “rough” at places, featuring Russian comments, empty catch blocks, and inconsistent error handling.
What really makes this new MaaS stand out is its distribution model, specifically the promise to pass the Chrome Web Store review and get malicious extensions onto the largest platform of trusted browser add-ons.
Given that such extensions continue to slip through the cracks, as recently highlighted in two separate reports by Symantec and LayerX, users should install only the minimum number of extensions they need, read user reviews, and confirm the publisher’s trustworthiness.

It’s budget season! Over 300 CISOs and security leaders have shared how they’re planning, spending, and prioritizing for the year ahead. This report compiles their insights, allowing readers to benchmark strategies, identify emerging trends, and compare their priorities as they head into 2026.
Learn how top leaders are turning investment into measurable impact.
