Microsoft plans to enhance the security of the Entra ID authentication system against external script injection attacks starting in mid-to-late October 2026.
This update will implement a strengthened Content Security Policy that allows script downloads only from Microsoft-trusted content delivery network domains and inline script execution only from Microsoft-trusted sources during sign-ins.
After rollout, it will protect users against various security risks, including cross-site scripting attacks in which attackers inject malicious code into websites to steal credentials or compromise systems.

The update policy will apply only to browser-based sign-in experiences at URLs beginning with login.microsoftonline.com, and Microsoft Entra External ID will not be affected.
“This update strengthens security and adds an extra layer of protection by allowing only scripts from trusted Microsoft domains to run during authentication, blocking unauthorized or injected code from executing during the sign-in experience,” said Megna Kokkalera, product manager for Microsoft Identity and Authentication Experiences.
Microsoft urged organizations to test sign-in scenarios before the October 2026 deadline to identify and address any dependencies on code-injection tools.
IT administrators can identify potential impact by reviewing sign-in flows in the browser developer console: violations will appear in red text with details about the blocked scripts.
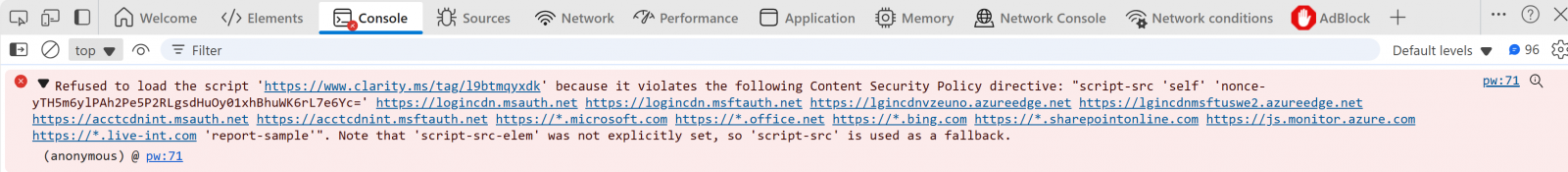
Microsoft also advised enterprise customers to stop using browser extensions and tools that inject code or scripts into sign-in pages before the change takes effect. These will no longer be supported and will stop working, although users will still be able to sign in.
“This update to our Content Security Policy adds an additional layer of protection by blocking unauthorized scripts, further helping safeguard your organization against evolving security threats,” Kokkalera added.
This move is part of Microsoft’s Secure Future Initiative (SFI), a company-wide effort launched two years ago, in November 2023, following a report from the Cyber Safety Review Board of the U.S. Department of Homeland Security, which found that the company’s security culture was “inadequate and requires an overhaul.”
As part of the same initiative, Microsoft also updated Microsoft 365 security defaults to block access to SharePoint, OneDrive, and Office files via legacy authentication protocols, disabled all ActiveX controls in Windows versions of Microsoft 365 and Office 2024 apps.
Earlier this month, it also began rolling out a new Teams feature announced in May and designed to block screen capture attempts during meetings.

As MCP (Model Context Protocol) becomes the standard for connecting LLMs to tools and data, security teams are moving fast to keep these new services safe.
This free cheat sheet outlines 7 best practices you can start using today.
