Microsoft announced that it will disable the 30-year-old NTLM authentication protocol by default in upcoming Windows releases due to security vulnerabilities that expose organizations to cyberattacks.
NTLM (short for New Technology LAN Manager) is a challenge-response authentication protocol introduced in 1993 with Windows NT 3.1 and is the successor to the LAN Manager (LM) protocol.
Kerberos has superseded NTLM and is now the current default protocol for domain-connected devices running Windows 2000 or later. While it was the default protocol in older Windows versions, NTLM is still used today as a fallback authentication method when Kerberos is unavailable, even though it uses weak cryptography and is vulnerable to attacks.

Since its release, NTLM has been widely exploited in NTLM relay attacks (where threat actors force compromised network devices to authenticate against attacker-controlled servers) to escalate privileges and take complete control over the Windows domain. Despite this, NTLM is still used on Windows servers, allowing attackers to exploit vulnerabilities such as PetitPotam, ShadowCoerce, DFSCoerce, and RemotePotato0 to bypass NTLM relay attack mitigations.
NTLM has also been targeted by pass-the-hash attacks, in which cybercriminals exploit system vulnerabilities or deploy malicious software to steal NTLM hashes (hashed passwords) from targeted systems. These hashed passwords are used to authenticate as the compromised user, allowing the attackers to steal sensitive data and spread laterally across the network.
“Blocked and no longer used automatically”
On Thursday, as part of a broader push toward passwordless, phishing-resistant authentication methods, Microsoft announced that NTLM will finally be disabled by default in the next major Windows Server release and associated Windows client versions, marking a significant shift away from the legacy protocol to more secure Kerberos-based authentication.
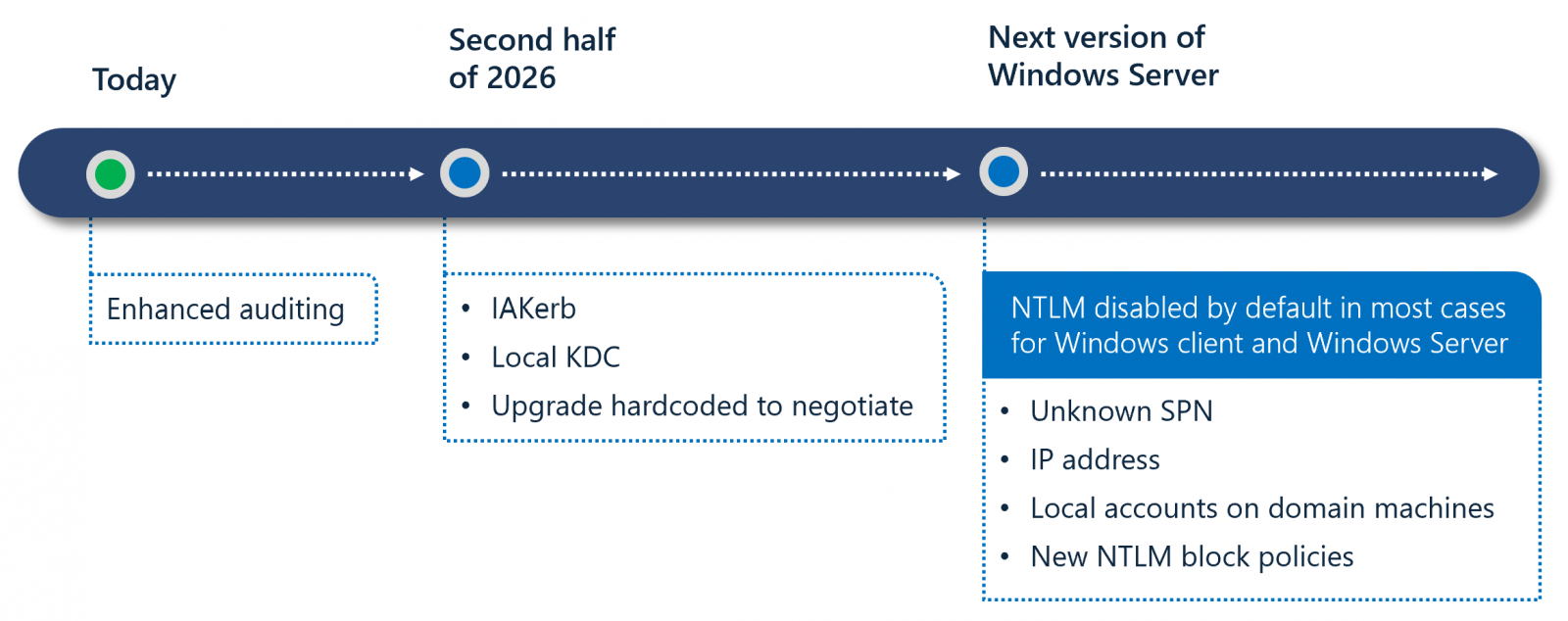
Microsoft also outlined a three-phase transition plan designed to mitigate NTLM-related risks while minimizing disruption. In phase one, admins will be able to use enhanced auditing tools available in Windows 11 24H2 and Windows Server 2025 to identify where NTLM is still in use.
Phase two, scheduled for the second half of 2026, will introduce new features, such as IAKerb and a Local Key Distribution Center, to address common scenarios that trigger NTLM fallback.
Phase three will disable network NTLM by default in future releases, even though the protocol will remain present in the operating system and can be explicitly re-enabled through policy controls if needed.
”Disabling NTLM by default does not mean completely removing NTLM from Windows yet. Instead, it means that Windows will be delivered in a secure-by-default state where network NTLM authentication is blocked and no longer used automatically,” Microsoft said.
“The OS will prefer modern, more secure Kerberos-based alternatives. At the same time, common legacy scenarios will be addressed through new upcoming capabilities such as Local KDC and IAKerb (pre-release).”
Microsoft first announced plans to retire the NTLM authentication protocol in October 2023, noting that it also wanted to expand management controls to give administrators greater flexibility in monitoring and restricting NTLM usage within their environments.
It also officially deprecated NTLM authentication on Windows and Windows servers in July 2024, advising developers to transition to Kerberos or Negotiation authentication to prevent future issues.
Microsoft has been warning developers to stop using NTLM in their apps since 2010 and advising Windows admins to either disable NTLM or configure their servers to block NTLM relay attacks using Active Directory Certificate Services (AD CS).

Whether you’re cleaning up old keys or setting guardrails for AI-generated code, this guide helps your team build securely from the start.
Get the cheat sheet and take the guesswork out of secrets management.
