A fake 7-Zip website is distributing a trojanized installer of the popular archiving tool that turns the user’s computer into a residential proxy node.
Residential proxy networks use home user devices to route traffic with the goal of evading blocks and performing various malicious activities such as credential stuffing, phishing, and malware distribution.
The new campaign became better known after a user reported that they downloaded a malicious installer from a website impersonating the 7-Zip project while following instructions in a YouTube tutorial on building a PC system. BleepingComputer can confirm that the malicious website, 7zip[.]com, is still live.

The threat actor registered the domain 7zip[.]com (still live at the time of writing) that can easily trick users into thinking they landed on the site of the legitimate tool.
Furthermore, the attacker copied the text and mimicked the structure of the original 7-Zip website located at 7-zip.org.
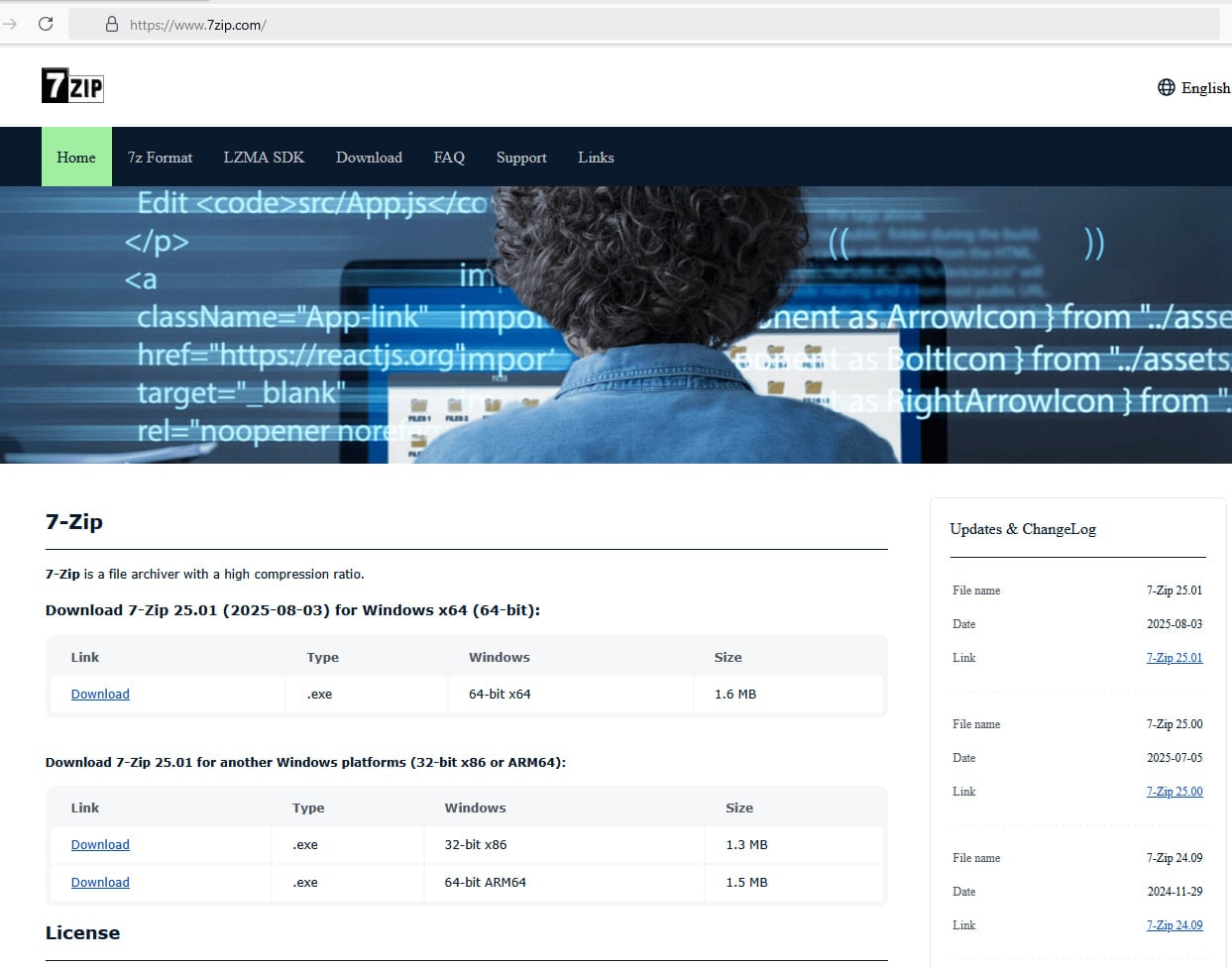
Source: BleepingComputer
The installer file was analyzed by researchers at cybersecurity company Malwarebytes, who found that it is digitally signed with a now-revoked certificate originally issued to Jozeal Network Technology Co., Limited.
The malicious copy also contains the 7-Zip program, thus providing the regular functions of the tool. However, the installer drops three malicious files:
- Uphero.exe – service manager and update loader
- hero.exe – main proxy payload
- hero.dll – support library
These files are placed in the ‘C:\Windows\SysWOW64\hero\’ directory, and an auto-start Windows service running as SYSTEM is created for the two malicious executables.
Additionally, firewall rules are modified using ‘netsh’ to allow the binaries to establish inbound and outbound connections.
Eventually, the host system is profiled with Microsoft’s Windows Management Instrumentation (WMI) and Windows APIs to determine the hardware, memory, CPU, disk, and network characteristics. The collected data is then sent to ‘iplogger[.]org.’
“While initial indicators suggested backdoor‑style capabilities, further analysis revealed that the malware’s primary function is proxyware,” Malwarebytes explains about the malware’s operational goal.
“The infected host is enrolled as a residential proxy node, allowing third parties to route traffic through the victim’s IP address.”
According to the analysis, hero.exe pulls config from rotating “smshero”-themed C2 domains, then opens outbound proxy connections on non-standard ports such as 1000 and 1002. Control messages are obfuscated using a lightweight XOR key.
Malwarebytes found that the campaign is larger than the 7-Zip lure and also uses trojanized installers for HolaVPN, TikTok, WhatsApp, and Wire VPN.
The malware uses a rotating C2 infrastructure built around hero/smshero domains, with traffic going through the Cloudflare infrastructure and carried over TLS-encrypted HTTPs.
It also relies on DNS-over-HTTPS via Google’s resolver, which reduces visibility for defenders monitoring standard DNS traffic.
The malware also checks for virtualization platforms such as VMware, VirtualBox, QEMU, Parallels, as well as for debuggers, to identify when it’s being analyzed.
Malwarebytes’ investigation started after noticing research from independent security researchers who analyzed the malware and uncovered its true purpose. Researcher Luke Acha discovered the purpose of the Uphero/hero malware.
The xor-based communication protocol was reverse-engineered and decoded by s1dhy, who confirmed the proxy behavior. Digital forensics and incident response (DFIR) engineer Andrew Danis connected the fake 7-Zip installer to the larger campaign impersonating multiple software brands.
Malwarebytes lists indicators of compromise (domains, file paths, IP addresses) and host-related data observed during their analysis.
Users are recommended to avoid following URLs from YouTube videos or promoted search results, and instead bookmark the download portal domains for the software they use often.

Modern IT infrastructure moves faster than manual workflows can handle.
In this new Tines guide, learn how your team can reduce hidden manual delays, improve reliability through automated response, and build and scale intelligent workflows on top of tools you already use.
