Table of Contents
Iranian hackers likely started a cyber espionage campaign just one week after the start of the Israel-Iran conflict in June.
In a new report published on July 21, cybersecurity firm Lookout shared findings about four new samples of DCHSpy, an Android surveillance tool leveraged by the Iranian cyber espionage group MuddyWater.
The new campaign appears to leverage lures centered around Starlink, the satellite internet service owned by Elon Musk’s SpaceX, to deploy the new DCHSpy versions.
Starlink offered internet access to Iranians during the imposed internet outage in July as a result of escalating hostilities between Iran and Israel.
Background on DCHSpy, a SandStrike Variant
DCHSpy is an Android surveillanceware family that has been active since at least 2024.
It shares infrastructure with another Android malware known as SandStrike, an Android surveillance tool first reported by Kaspersky in 2022 targeting practitioners of the Baháʼí Faith, a religion practiced in Iran and parts of the Middle East.
Like SandStrike, DCHSpy is likely developed and maintained by MuddyWater, an advanced persistent threat (APT) group believed to be affiliated with Iran’s Ministry of Intelligence and Security.
DCHSpy typically uses political lures and disguises as legitimate apps, such as VPNs or banking applications.
DCHSpy, 2025 Version: New Lures, New Capabilities
While previous DCHSpy samples leveraged a seemingly legitimate VPN solution called HideVPN, the four new DCHSpy samples identified by Lookout impersonate two new VPN apps, EarthVPN and ComodoVPN.
The former claims to be a Romania-based VPN solution and the latter located in Canada.
These three apps, as well as an app called ‘Hazrat Eshq,’ are advertised on various Telegram channels to English and Farsi speakers, using anti-Iran themes and language.
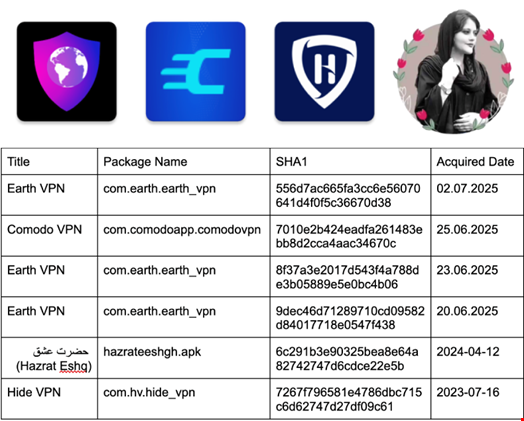
One of the Earth VPN samples was uploaded with an Android Package (APK) filename that included a reference to Starlink. They list addresses and contact numbers belonging to random businesses in those respective countries.
“This may indicate that DCHSpy VPN samples are also being spread with Starlink lures, especially given recent reports of Starlink offering internet services to the Iranian population during the internet outage imposed by the Iranian government following hostilities between Israel and Iran,” the Lookout report said.
Once deployed, the new DCHSpy samples collect a wider range of information on the target device than previous samples. These include:
- Accounts logged into on the device
- Contacts
- SMS messages
- Files stored on the device
- Location data
- Call logs
- WhatsApp data
- Audio by taking control of the microphone
- Photos by taking control of the camera
“These most recent samples of DCHSpy indicate continued development and usage of the surveillanceware as the situation in the Middle East evolves, especially as Iran cracks down on its citizens following the ceasefire with Israel,” said the Lookout report.
17 Mobile Malware Strains Identified, Tied to 10 Iranian APT Groups
The mobile cybersecurity firm has identified 17 mobile malware families that at least 10 Iranian APTs have been using in surveillance attacks against mobile phone users.
These include SandStrike and DCHSP, as well as BouldSpy, which was used by the Law Enforcement Command of the Islamic Republic of Iran in 2023, and GuardZoo, tied to the Yemen-based Houthis, who are aligned with the Iranian regime.
Lookout has also observed Iranian APT groups leveraging commodity spyware, such as Metasploit, AndroRat, AhMyth and SpyMax, to deploy cyber espionage campaigns.
