Threat actors exploited a recently patched remote code execution vulnerability (CVE-2025-20352) in Cisco networking devices to deploy a rootkit and target unprotected Linux systems.
The security issue leveraged in the attacks affects the Simple Network Management Protocol (SNMP) in Cisco IOS and IOS XE and leads to RCE if the attacker has root privileges.
According to cybersecurity company Trend Micro, the attacks exploited the flaw in Cisco 9400, 9300, and legacy 3750G series devices and deployed rootkits on “older Linux systems that do not have endpoint detection response solutions.”
In the original bulletin for CVE-2025-20352, updated on October 6, Cisco tagged the vulnerability as exploited as a zero day, with the company’s Product Security Incident Response Team (PSIRT) saying it was “aware of successful exploitation.”
Trend Micro researchers track the attacks under the name ‘Operation Zero Disco’ because the malware sets a universal access password that contains the word “disco.”
The report from Trend Micro notes that the threat actor also attempted to exploit CVE-2017-3881, a seven-year-old vulnerability in the Cluster Management Protocol code in IOS and IOS XE.
The rootkit planted on vulnerable Cisco devices features a UDP controller that can listen on any port, toggle or delete logs, bypass AAA and VTY ACLs, enable/disable the universal password, hide running configuration items, and reset the last write timestamp for them.
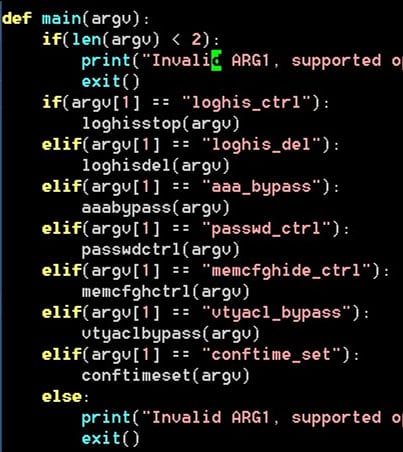
Source: Trend Micro
In a simulated attack, the researchers showed that it is possible to disable logging, impersonate a waystation IP via ARP spoofing, bypass internal firewall rules, and move laterally between VLANs.
.jpg)
Source: Trend Micro
Although newer switches are more resistant to these attacks due to Address Space Layout Randomization (ASLR) protection, Trend Micro says that they are not immune and persistent targeting could compromise them.
After deploying the rootkit, the malware “installs several hooks onto the IOSd, which results in fileless components disappearing after a reboot,” the researchers say.
The researchers were able to recover both 32-bit and 64-bit variants of the SNMP exploit.
Trend Micro notes that there currently exists no tool that can reliably flag a compromised Cisco switch from these attacks. If there is suspicion of a hack, the recommendation is to perform a low-level firmware and ROM region investigation.
A list of the indicators of compromise (IoCs) associated with ‘Operation Zero Disco’ can be found here.
Update [Oct 17, 06:16 EST]: Article edited to clarify that the lack of endpoint detection and response protection referred to older Linux systems.

46% of environments had passwords cracked, nearly doubling from 25% last year.
Get the Picus Blue Report 2025 now for a comprehensive look at more findings on prevention, detection, and data exfiltration trends.
