Threat actors are abusing SourceForge to distribute fake Microsoft add-ins that install malware on victims’ computers to both mine and steal cryptocurrency.
SourceForge.net is a legitimate software hosting and distribution platform that also supports version control, bug tracking, and dedicated forums/wikis, making it very popular among open-source project communities.
Although its open project submission model gives plenty of margin for abuse, actually seeing malware distributed through it is a rare occurrence.
The new campaign spotted by Kaspersky has impacted over 4,604 systems, most of which are in Russia.
While the malicious project is no longer available on SourceForge, Kaspersky says the project had been indexed by search engines, bringing traffic from users searching for “office add-ins” or similar.

Source: Kaspersky
Fake Office add-ins
The “officepackage” project presents itself as a collection of Office Add-in development tools, with its description and files being a copy of the legitimate Microsoft project ‘Office-Addin-Scripts,’ available on GitHub.
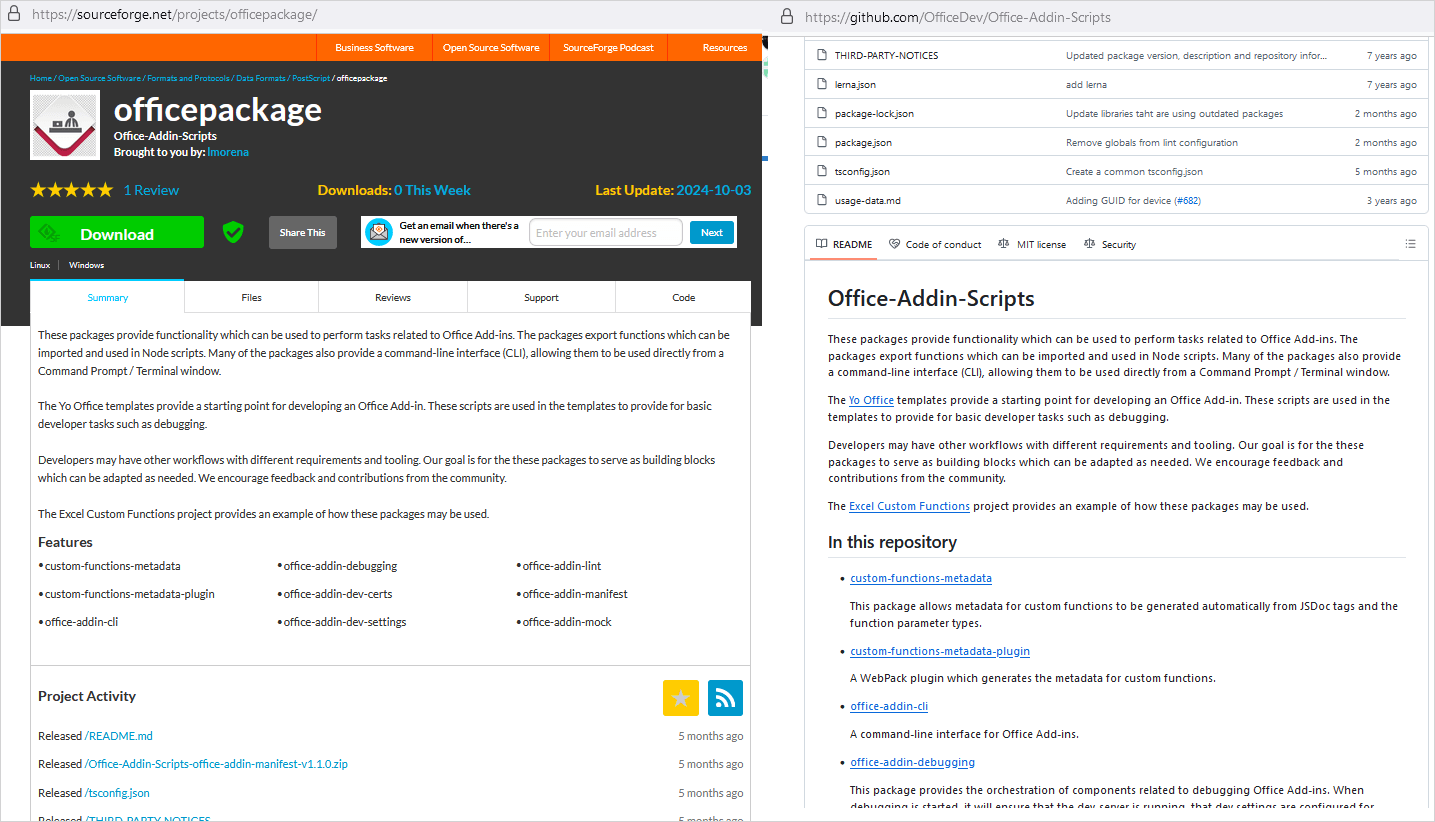
Source: Kaspersky
However, when users search for office add-ins on Google Search (and other engines), they get results pointing to “officepackage.sourceforge.io,” powered by a separate web hosting feature SourceForge gives to project owners.
That page mimics a legit developer tool page, showing the “Office Add-ins” and “Download” buttons. If any are clicked, the victim receives a ZIP containing a password-protected archive (installer.zip) and a text file with the password.
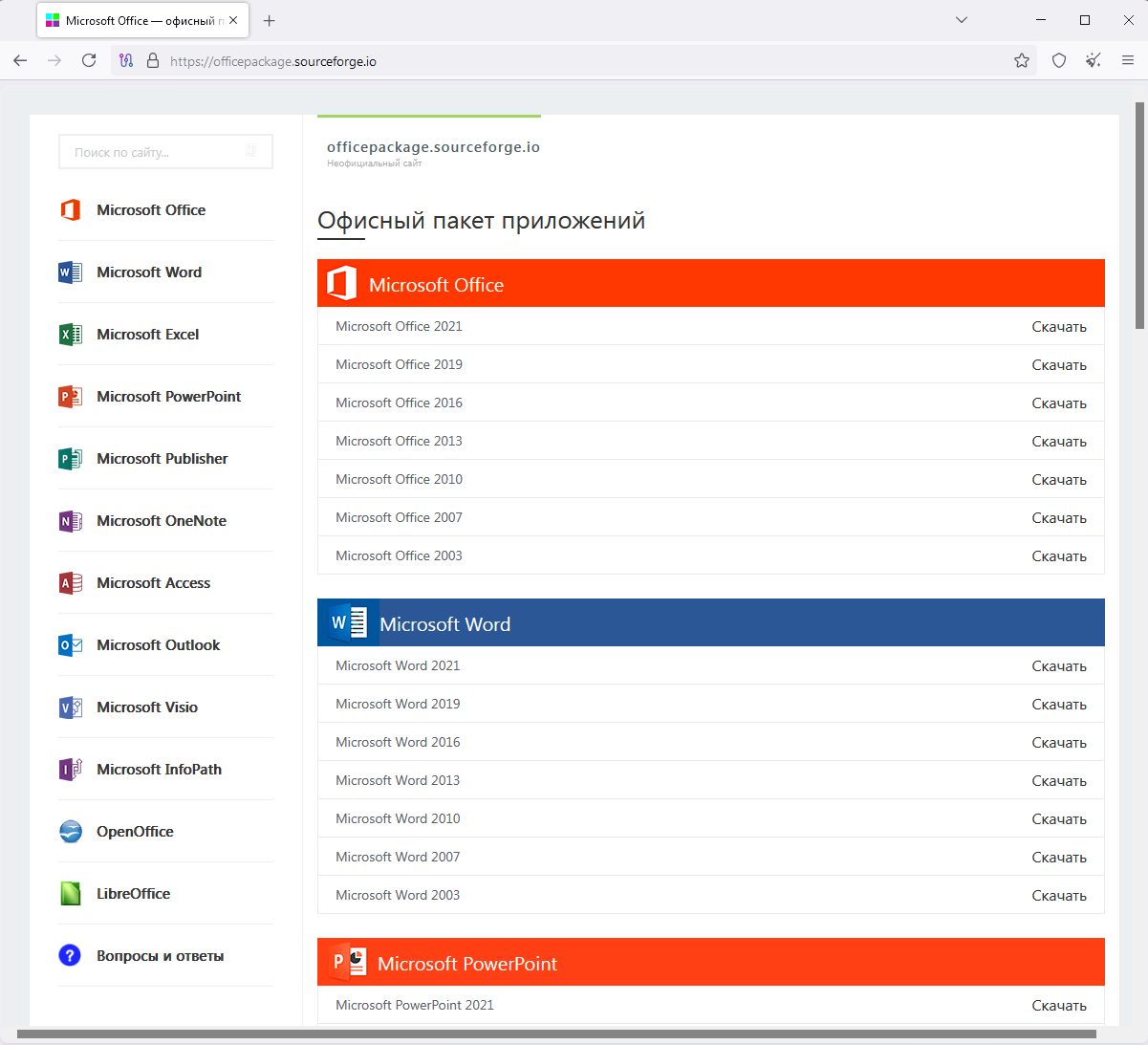
Source: BleepingComputer
The archive contains an MSI file (installer.msi) inflated to 700MB in size to evade AV scans. Running it drops ‘UnRAR.exe’ and ‘51654.rar,’ and executes a Visual Basic script that fetches a batch script (confvk.bat) from GitHub.
The script performs checks to determine whether it runs on a simulated environment and what antivirus products are active, and then downloads another batch script (confvz.bat) and unpacks the RAR archive.
The confvz.bat script establishes persistence via Registry modifications and the addition of Windows services.
The RAR file contains an AutoIT interpreter (Input.exe), the Netcat reverse shell tool (ShellExperienceHost.exe), and two payloads (Icon.dll and Kape.dll).
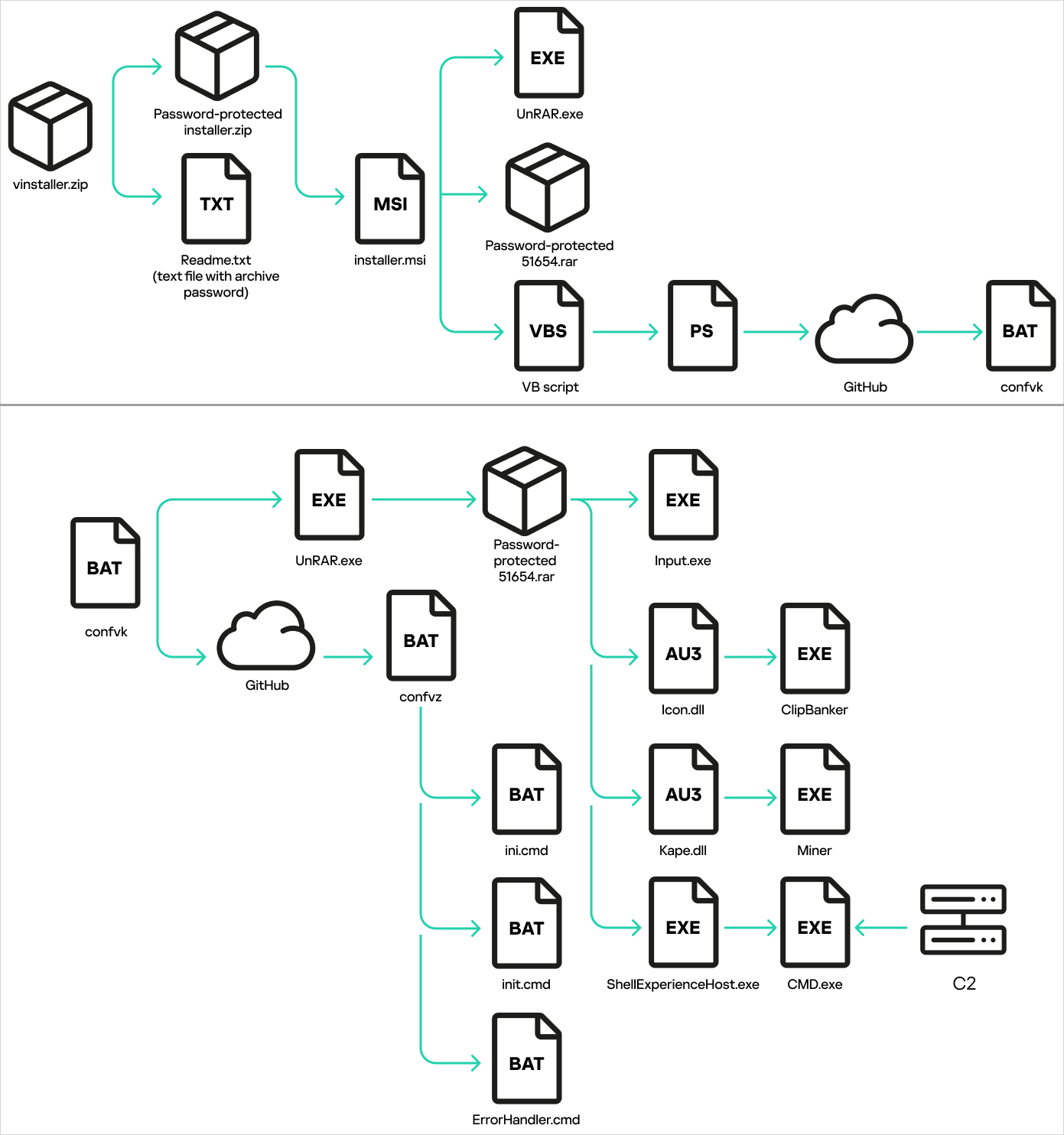
Source: Kaspersky
The DLL files are a cryptocurrency miner and a clipper. The former hijacks the machine’s computational power to mine cryptocurrency for the attacker’s account, and the latter monitors the clipboard for copied cryptocurrency addresses and replaces them with attacker-controlled ones.
The attacker also receives the infected system’s information via Telegram API calls and can use the same channel to introduce additional payloads to the compromised machine.
This campaign is another example of threat actors exploiting any legitimate platform to gain false legitimacy and bypass protections.
Users are recommended to only download software from trusted publishers who they can verify, prefer the official project channels (in this case GitHub), and scan all downloaded files with an up-to-date AV tool before execution.

Based on an analysis of 14M malicious actions, discover the top 10 MITRE ATT&CK techniques behind 93% of attacks and how to defend against them.
