Table of Contents
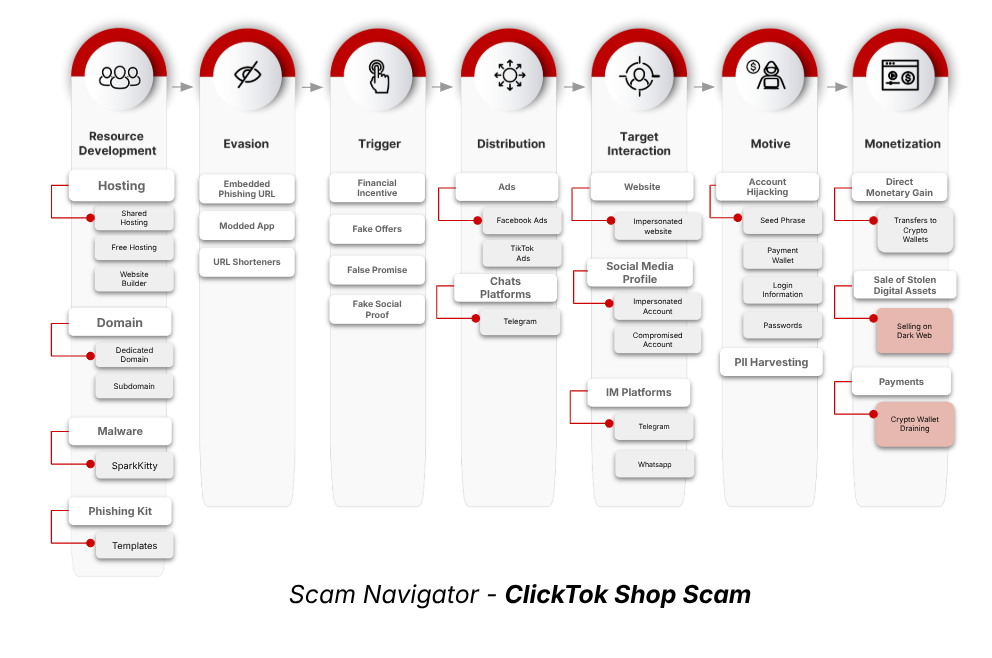
CTM360 has discovered a new global malware campaign dubbed “ClickTok” that spreads the SparkKitty spyware through fake TikTok shops to steal cryptocurrency wallets and drain funds.
The unique unique spyware trojan discovered by CTM360 is specifically engineered to exploit TikTok Shop users across the globe.
Dubbed as “ClickTok”, this highly coordinated scam operation employs a hybrid scam model that combines phishing and malware to deceive buyers and affiliate program participants on TikTok’s growing e-commerce platform.
In the ClickTok campaign, TikTok shops were identified embedded with SparkKitty spyware, a variant closely resembling SparkCat, previously identified by Kaspersky.
Once installed, it infiltrates the user’s device, accesses the photo gallery, and extracts screenshots that may contain cryptocurrency wallet credentials. What makes ClickTok unique is its simultaneous use of phishing and malware tactics, significantly increasing its impact and stealth.
The scam begins with the impersonation of TikTok’s commercial ecosystem, including TikTok Shop, TikTok Wholesale, and TikTok Mall. Threat actors create fake TikTok websites that closely mimic the official interface, deceiving users into thinking they’re interacting with the real platform.
Victims are lured into logging in and attempting to make purchases. During the checkout process, they are instructed to pay via cryptocurrency wallets.
Once payment is made, the trojanized app embedded with SparkKitty spyware, covertly captures sensitive data, including wallet credentials, by reading screenshots and images stored on the device, ultimately enabling the theft of digital funds.
The Motive Behind ClickTok – A Hybrid Scam Structure
The attacker has two main objectives:
Phishing Websites:
They incite users to open the fake Shop URLs distributed through meta ads, prompting users to enter login credentials, payment details, or seller information, all of which are silently harvested.
CTM360 has tracked down a unique spyware trojan specifically engineered to exploit TikTok Shop users across the globe.
Dubbed as “ClickTok”, this highly coordinated scam operation employs a hybrid scam model that combines phishing and malware to deceive buyers and affiliate program participants on TikTok’s growing e-commerce platform.
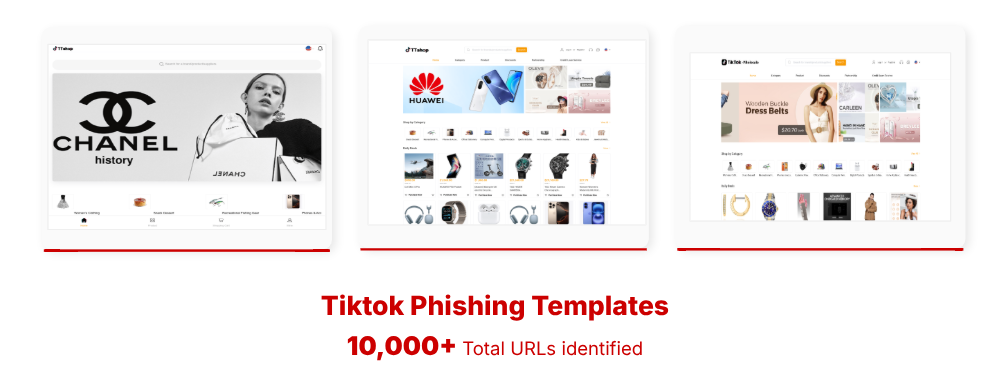
Trojanized Apps:
On mobile, the sites urge users to install modified TikTok Apps that are infected with SparkKitty, a malicious spyware variant capable of deep device surveillance, clipboard scraping, and credential theft.
These fake apps have the exact user interfaces as original TikTok shops, tricking victims into believing they’re interacting with a legitimate TikTok App while silently siphoning sensitive data in the background.
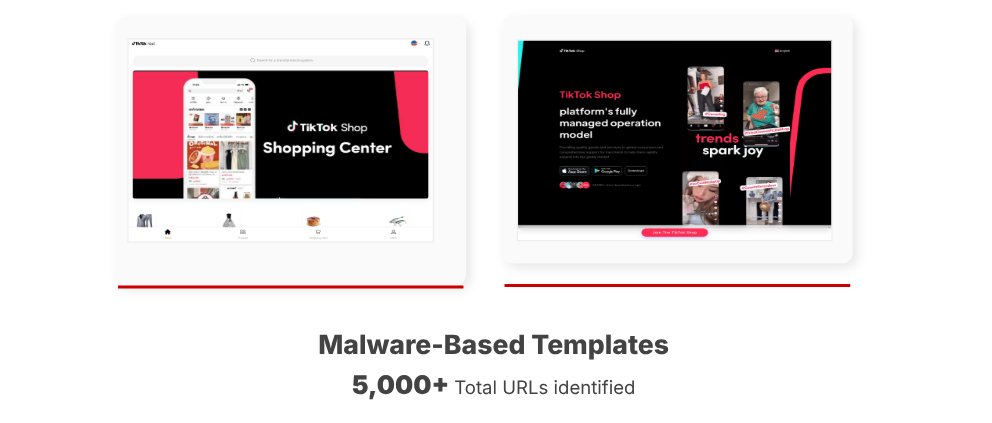
Fake Ads, AI Videos & Lookalike Domains
ClickTok scammers use Fake AI-generated Videos and Meta ads to reach a wider audience. These ads direct users to fake cybersquatted domains carefully crafted to look like real TikTok URLs.
To date, CTM360 has observed:
-
10,000+ impersonated TikTok websites, many using free or inexpensive TLDs such as .top, .shop, .icu, and others.
-
Over 5,000+ unique malicious app instances, spread via QR codes, messaging apps, and in-app downloads.
Fraudulent campaigns impersonating not just TikTok Shop, but also TikTok Wholesale and TikTok Mall.
Motive & Monetization
The ClickTok campaign uses fake TikTok Shop login pages to harvest user credentials and malware distribution through trojanized apps that enable account hijacking. It implements an alternative payment structure that excludes traditional card transactions, instead requiring payments through cryptocurrency wallets.
Victims are often encouraged to “top up” fake TikTok wallets or digital currencies like USDT, ETH and more.
CTM360’s Recommendations
CTM360 urges users and organizations to stay vigilant and take the following precautions:
-
Avoid downloading modded, cracked, or unknown software, especially from torrent sites and Telegram.
-
Always verify domain authenticity before entering login or payment information, and manually check for spelling errors or suspicious domain extensions.
-
Report any suspicious TikTok-related content, ads, or apps directly to TikTok or cybersecurity authorities in your country.
-
Brands and sellers should regularly monitor brand abuse and impersonation trends using threat intelligence platforms.
-
Strong antivirus or EDR Solution to prevent SparkKitty spyware breaches.
-
If you use a crypto wallet, go for one that is clipboard-protected.
Read the full ClickTok SparkKitty Report.
CTM360 has run a deep analysis of the ClickTok scam and published a detailed report on the ClickTok trojan.
Read the full ClickTok report
Detect Cyber Threats 24/7 with CTM360
Monitor, analyze, and promptly mitigate risks across your external digital landscape with the CTM360.
Join our Community Edition
Sponsored and written by CTM360.
