Table of Contents
The Cybersecurity Maturity Model Certification’s (CMMC) reality check has arrived.
After years of delays and speculation, enforcement moves from theory to action in November 2025 (next month as of this writing!).
If you handle Controlled Unclassified Information (CUI), the clock is already running. This is not a slide deck problem! It is an operational risk that touches contracts, revenue, and reputation.
The milestones that matter are clear.
The Department of Defense published the final CMMC program rule in October 2024 and it became effective in December 2024.
The separate Defense Federal Acquisition Regulation Supplement (DFARS) rule that enables contracting officers to enforce CMMC was finalized on September 10, 2025, with enforcement beginning November 10, 2025.
The rollout is phased. Phase 1 starts November 10, 2025. Phase 2 starts November 10, 2026. Full coverage arrives by November 10, 2028.
There is no reason to expect more extensions, and many program offices and prime contractors are already asking for proof of maturity before they award work. Treat the next few quarters as a countdown, not a debate.
Figure1: CMMC Timelines 2018 – 2032
What Has Actually Changed and Why It Matters
The most significant change is not a control list. It is the end of ambiguity. The CMMC program rule is final and in effect, and the acquisition rule that inserts CMMC language into your contracts is final with dated enforcement. The four phase sequence makes timing explicit.
- Phase 1: Beginning November 10, 2025, program offices can include CMMC at their discretion.
- Phase 2: Beginning November 10, 2026, most organizations handling CUI will require third-party Level 2 assessments.
- Phase 3 and Phase 4 culminate with full coverage by November 10, 2028.
Across the industrial base, this ends the “wait and see” posture. The capacity problem that many hoped would disappear has not. It is the constraint you must manage.
The Scale Problem Everyone Now Feels
The market faces a familiar supply and demand imbalance. There are far fewer qualified assessors than companies that will need Level 2. Even with aggressive training, the pipeline cannot double overnight. That creates backlogs and raises prices, especially for firms that want veteran Certified 3rd Party Assessor Organizations (C3PAOs) and Certified CMMC Assessor (CCAs). The result is lead times that stretch into quarters, not weeks.
A simple lens helps you avoid the scramble:
- Scope first.
- Automate fundamentals that produce durable evidence.
- Build your evidence as you go.
- Run a readiness review against the assessment guide.
- Fix what breaks under pressure, then schedule a C3PAO who is comfortable with your size and architecture.
Broader Challenges That Slow Implementation
There are three (3) recurring sources of friction.
Structural separation between consulting and assessment. The ecosystem enforces conflict rules. A C3PAO cannot consult for the same company it assesses, and advisory firms cannot assess their own clients. That separation protects integrity, but it adds coordination overhead. Strong programs keep a clean line between builders and validators and choreograph the handoff well before assessment day.
Workforce and quality. The number of assessors has grown, but not enough to erase bottlenecks. Quality matters as much as quantity. Inexperienced assessors can turn a two (2) week event into a six (6) week grind. The same risk exists on the advisory side. Choose partners with repeatable playbooks and references from organizations similar to yours.
Small business reality. Many Defense Industrial Base (DIB) firms operate with lean IT teams and tight budgets. They cannot pause operations to write every policy and deploy every control in one sprint. They need sequencing that produces weekly evidence without breaking production. This is where approach matters more than slogans.
Controversies And Governance Lessons Contractors Should Internalize
The CMMC push has unfolded amid a swirl of industry activity and some unwelcome headlines. The CEO of Blue Forge has stepped-down from his position and broader governance concerns have created noise across defense circles. Whether or not a specific entity remains in the spotlight next month, the lesson is durable. Do not anchor your compliance schedule to hype, branding, or a personality. Anchor it to governance, evidence, and partners who will still be standing when the audit starts.
Ask for proof of delivery and examples that align to the CMMC assessment guide. Ask for references from companies of your size. Verify who does the work and who signs reports. If leadership is distracted or under scrutiny, your timelines and reputation are at risk.
A Lean Pathway to Level 2 That Survives Audit Pressure
A company tackling the CMMC challenge head-on is a boutique company called CloudRaider based near Atlanta. CloudRaider.ai’s method is to make the work boring and predictable. Audits reward boring.
Scope The Environment
Identify where CUI lives, who can touch it, and how it moves. Minimize the boundary. Use a dedicated enclave where it reduces complexity. Smaller scope lowers cost and shortens the path to evidence.
Design To the Controls
For each NIST SP 800-171 requirement, define the technical configuration, the operating procedure, and the proof. Link them in a single evidence register. If you cannot show it on screen or export it on demand, it does not count. Build that muscle from day one.
Automate The Baselines
Identity and access hygiene, endpoint configuration, vulnerability scanning and remediation, logging and alerting with meaningful retention. Automation shortens the path to evidence and reduces human error.
Sequence Realistically
Fix the highest risk items first. Roll-out administrative multifactor authentication everywhere. Provide least privilege for service accounts with managed secrets. Enforce encryption at rest and in transit with documented key handling. Provide logging that a named role reviews on a schedule. Deliver vulnerability findings that move through a triage queue and close against a service level objective. Prove these habits with timestamps and change records.
Rehearse
A readiness review is where weak documentation and inconsistent practice get exposed. That is a good thing. Run the review with a critical friend or a former assessor. Time box sessions. Train control owners to present evidence fast. The discomfort you invite in rehearsal disappears under the real spotlight.
What Must Be True by Enforcement
When enforcement begins in November 2025, a credible Level 2 shop should be able to demonstrate five things on demand.
- A current scope and SSP that an outsider can read without a tour guide. Include up-to-date diagrams, data flows, and inventories.
- Enforced technical baselines that match policy. Identity, access, endpoint, encryption, logging, and backups are configured to defined baselines and verified. Drift is detected and corrected.
- Operating procedures with names and frequencies. People know who does what and on what cadence. The last several runs are documented and accessible. Exceptions are tracked and resolved.
- A continuous improvement loop. Findings from scans, incidents, tests, and audits flow into a Plan of Action and Milestones with owners and dates. Executives see progress and remove blockers.
- Evidence packages that match the assessor’s lens. For each requirement, there is a small set of screenshots, exports, and logs with timestamps and system identifiers. The package is current and easy to navigate.
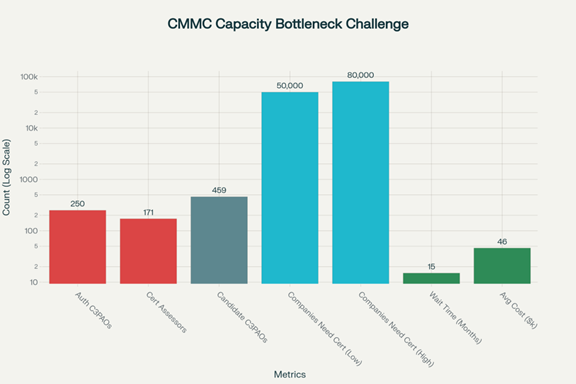
Figure 2: CMMC Capacity Bottleneck Challenge
A Case Study: Cloudraider.ai’s Delivery Kit
Repeatability wins. CloudRaider.ai’s kit, for example, includes a scoping and boundary playbook, a single evidence register, templates for every required plan and procedure, a vault of example screenshots and exports with redaction guidance, a cadence calendar for recurring tasks, and a readiness review script that trains control owners.
It also maps common tool outputs to specific control statements so that reporting to executives and primes is quick.
The kit flexes to the client. If logging and vulnerability management are solid, the plan shifts to identity cleanup and data handling. If a separate enclave reduces scope, the plan starts there. The goal is a first-pass success and a program the team can run without consultants sitting in every meeting.
Operations Discipline and Contracting Mechanics
Execution does not happen in a vacuum. Contracting mechanics must be ready so wins can be booked when opportunity knocks.
As David Bell, CloudRaider.ai’s Business Development Manager put it recently, the work needs “the next two or three action items – who’s doing them and by when” so that momentum converts into booked work. He stressed making sure you “have a contractual basis to move forward and… secure these contracts without any hiccups.”
Practical steps include getting registrations in order, aligning your General Services Administration (GSA) strategy, and building a federal-facing capability statement that speaks in a contracting officer’s language. Document the buying path so your prime can act without delay when you clear readiness.
CloudRaider.ai CEO and Founder Carric Dooley has emphasized internally that leadership focus is non-negotiable when calendars compress. His guidance shapes the approach described here: “scope with discipline, automate what matters, and rehearse under time pressure so the real assessment feels familiar”.
Ten traps that sink Level 2 programs
- Trying to fix everything at once. You cannot refactor identity, logging, backups, and documentation in parallel without breaking production. Sequence the work.
- Policy without configuration. Policies are not evidence. Proof lives in enforced settings and repeatable exports.
- Tool sprawl. Ten point products create ten shallow outputs. Fewer platforms with deeper coverage are easier to defend.
- Evidence that ages out. Screenshots without timestamps or system identifiers get tossed. Build exports you can refresh in minutes.
- Procedure theater. Procedures that nobody runs will fail a sample. Put names and dates on recurring tasks.
- No enclave. Keeping CUI in the same place as everything else inflates scope and cost. Minimize the boundary.
- Weak service account hygiene. Unbounded service identities and unmanaged keys are common findings.
- No POA&M discipline. Findings without owners and dates are a red flag. Track and burn down risk.
- Late assessor engagement. Waiting to meet your C3PAO until the last mile invites surprise. Align expectations early.
- Assuming primes will wait. Many primes are moving faster than the government timeline. Treat private sector pressure as real.
The 90 Day Execution Checklist
Week 1 to 2. Freeze scope and tooling. Create the evidence register. Draft diagrams and inventories for the SSP. Schedule identity cleanup and endpoint baselines.
Week 3 to 4. Enforce multifactor authentication on every admin plane. Lock down service accounts and rotate secrets. Configure encryption and backups and perform test restores. Turn on logging with retention and alerting. Draft the first wave of procedures and run them at least once.
Week 5 to 8. Close high risk findings. Stand up dashboards that show control status. Run a table top incident response and record lessons learned. Expand procedures to cover the full set. Hold an internal readiness review.
Week 9 to 10. Fix the weak spots. Harden documentation. Brief control owners on presenting evidence clearly. Confirm contracting mechanics and the path to purchase for your prime.
Week 11 to 12. Run a timed dress rehearsal. Package evidence by requirement. Lock dates with the assessor. Move remaining gaps to the POA&M with owners and due dates. Confirm executive sponsorship for the assessment window.
After Certification
Certification is a waypoint. People change jobs. Systems evolve. Customer requirements shift. Treat CMMC like safety or quality. Make it part of standard operations with metrics, reviews, and a budget. That discipline pays off at recompete time and when primes need reliable partners for complex bids.
The Bottom Line
CMMC is here and the calendar is tight! The companies that move now will have better contract access and quieter audits. The companies that wait will face longer queues and higher costs.
Choose partners who work lean and show proof.
Build a kit your team can sustain.
Turn every week between now and enforcement into measurable progress.
Do it now.
 Pete Green is the CISO / CTO of Anvil Works, a ProCloud SaaS company. With over 25 years of experience in information technology and cybersecurity, Pete is a seasoned and accomplished security practitioner.
Pete Green is the CISO / CTO of Anvil Works, a ProCloud SaaS company. With over 25 years of experience in information technology and cybersecurity, Pete is a seasoned and accomplished security practitioner.
Throughout his career, he has held a wide range of technical and leadership roles, including LAN/WLAN Engineer, Threat Analyst, Security Project Manager, Security Architect, Cloud Security Architect, Principal Security Consultant, Director of IT, CTO, CEO, Virtual CISO, and CISO.
Pete has supported clients across numerous industries, including federal, state, and local government, as well as financial services, healthcare, food services, manufacturing, technology, transportation, and hospitality.
He holds a Master of Computer Information Systems in Information Security from Boston University, which is recognized as a National Center of Academic Excellence in Information Assurance / Cyber Defense (CAE IA/CD) by the NSA and DHS. He also holds
