Table of Contents
deVixor: An Evolving Android Banking RAT with Ransomware Capabilities Targeting Iran
Cyble analyzed deVixor, an advanced Android banking RAT with ransomware features actively targeting Iranian users.
Executive Summary
deVixor is an actively developed Android banking malware campaign operating at scale, targeting Iranian users through phishing websites that masquerade as legitimate automotive businesses.
Distributed as malicious APK files, deVixor has evolved from a basic SMS-harvesting threat into a fully featured Remote Access Trojan (RAT) that combines banking fraud, credential theft, ransomware, and persistent device surveillance within a single platform.
Active since October 2025, Cyble Research and Intelligence Lab’s (CRIL) analysis of over 700 samples indicates with high confidence that the threat actor has been conducting a mass infection campaign leveraging Telegram-based infrastructure, enabling centralized control, rapid updates, and sustained campaign evolution.
Key Takeaways
- deVixor is a sophisticated Android banking trojan that combines financial data theft, device surveillance, and remote control into a single malware platform.
- The malware is actively distributed through fake websites posing as legitimate automotive businesses, tricking users into installing malicious APK files.
- deVixor extensively harvests SMS-based financial information, including OTPs, account balances, card numbers, and messages from banks and cryptocurrency exchanges.
- It leverages WebView-based JavaScript injection to capture banking credentials by loading legitimate banking pages inside a WebView.
- The malware includes a remotely triggered ransomware module capable of locking devices and demanding cryptocurrency payments.
- deVixor uses Firebase for command delivery and Telegram-based bot infrastructure for administration, allowing attackers to manage infections at scale and evade traditional detection mechanisms.
Overview
Android banking malware has progressed well beyond basic credential-harvesting threats, evolving into sophisticated remote access toolkits maintained as persistent, service-driven criminal operations.
During our ongoing analysis of malicious sites, we uncovered deVixor, a previously underreported Android Remote Access Trojan (RAT) actively distributed via fraudulent websites masquerading as legitimate automotive companies.
These sites lure victims with heavily discounted vehicle offers and trick them into downloading a malicious APK, which ultimately installs the deVixor malware on the device.

Some of the malicious URLs distributing deVixor RAT are:
- hxxp://asankhodroo[.]shop
- hxxp://www[.]asan-khodro.store
- hxxp://www[.]naftyar.info/naftman.apk
- hxxp://abfayar[.]info/abfa.apk
- hxxps://blupod[.]site/blupod.apk
- hxxps://naftman[.]oghabvip.ir/naftman.apk
- hxxp://vamino[.]online.infochatgpt.com/vamino.apk
- hxxps://lllgx[.]site/mm/V6.apk
CRIL identified more than 700 samples of multiple variants of the deVixor RAT from October 2025. Early versions of the malware exhibited limited functionality, primarily focused on collecting PII and harvesting banking-related SMS messages.
Subsequent variants showed a clear evolution in capabilities, introducing banking-focused overlay attacks, keylogging, ransomware attacks, Google Play Protect bypass techniques, and extensive abuse of Android’s Accessibility Service.
Our investigation also uncovered a Telegram channel operated by the threat actor, which was created shortly after the initial development of deVixor RAT and was actively used to publish version updates, promote new capabilities, and share operational screenshots.
Notably, screenshots posted in the channel reveal numerous devices that are simultaneously infected, each associated with a unique Bot ID (referred to by the actor as a “Port”), suggesting an active campaign operating at scale.
The channel’s growing subscriber base further supports the assessment that deVixor is being maintained and distributed as an ongoing criminal service rather than a short-lived operation. (See Figures 1, 2, and 3)
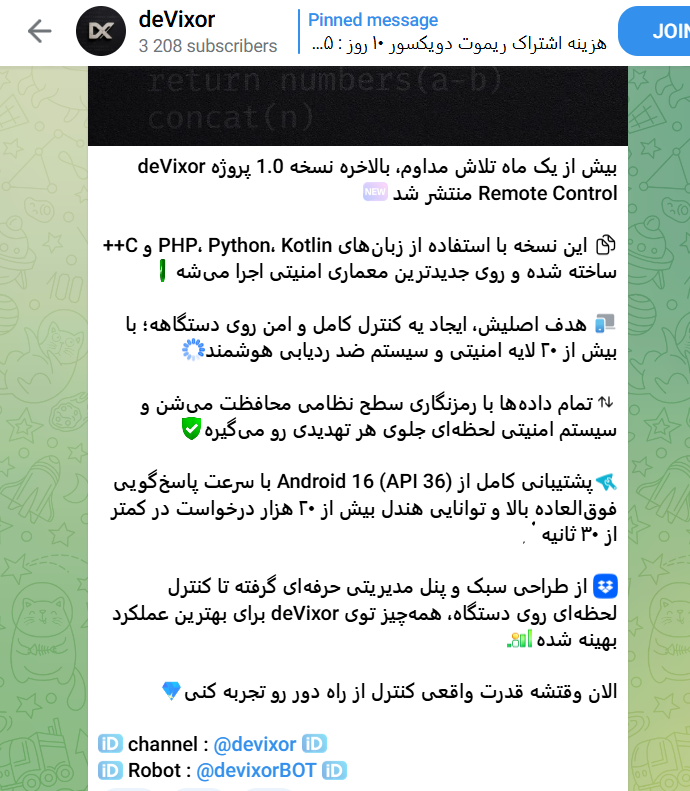


The deVixor RAT leverages a Telegram bot–based administrative panel for issuing commands. Each deployed APK is assigned a unique Bot ID stored in a local port.json file, enabling the operator to track, monitor, and control individual infected devices.
Once registered, the operator receives real-time updates via Telegram and can issue commands that are relayed to infected devices through backend infrastructure. Figure 4 illustrates the available administrative actions and operational updates as observed in the threat actor’s Telegram channel. (see Figure 4)
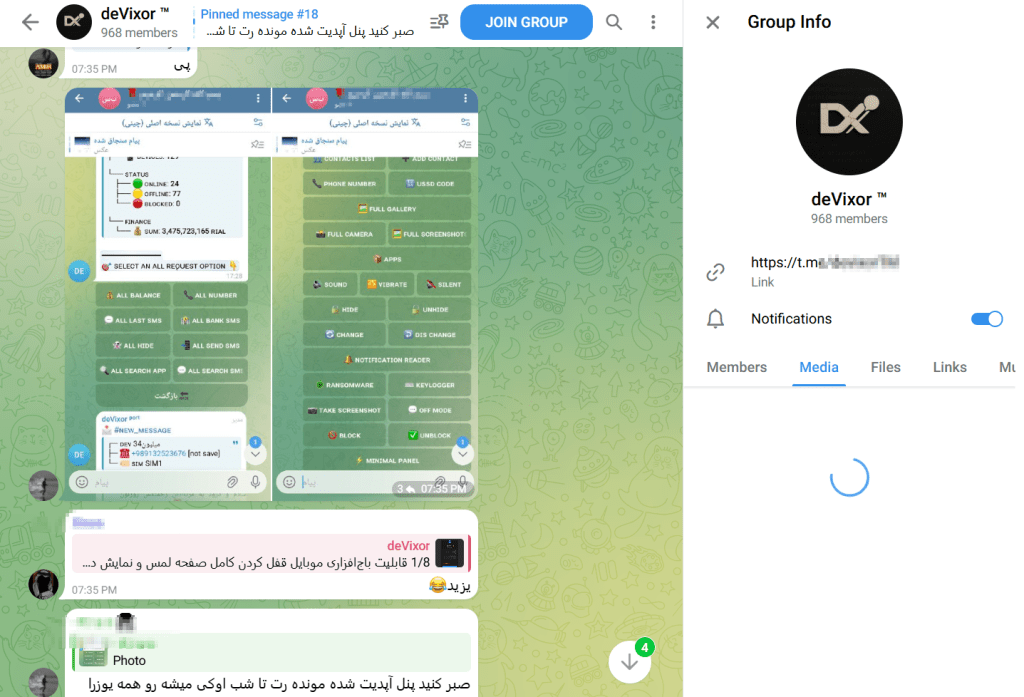
Multiple indicators suggest that the campaign is regionally focused. Linguistic artifacts observed in Telegram communications, operator messages, and hardcoded strings within the APK, combined with the exclusive targeting of Iranian banks, domestic payment services, and local cryptocurrency exchanges, strongly indicate that Iranian users are the primary targets of this operation. The use of Persian-language user interface elements in phishing overlays further reinforces this assessment.
DeVixor demonstrates how modern Android banking malware has evolved into a scalable, service-driven criminal platform capable of compromising devices over the long term and facilitating financial abuse.
Its active development, growing feature set, and reliance on legitimate platforms such as Telegram for command-and-control pose a significant risk to Android users. The next section provides a detailed technical analysis of deVixor RAT’s functionality, command structure, and abuse mechanisms observed across multiple variants.
Technical Analysis
Upon installation, the deVixor RAT prompts victims to grant permissions to access SMS messages, contacts, and files. In newer variants, it additionally requests Accessibility service permissions. (see Figure 5)

Once the required permissions are granted, the malware establishes communication with Firebase to receive commands from the threat actor. In parallel, deVixor decrypts a hardcoded alternate Command-and-Control (C&C) server URL, which is used to exfiltrate the collected data.
Overall, deVixor relies on two distinct servers for its operations: (see Figure 6)
- Firebase server – used for receiving commands
- C&C server – used for transmitting stolen data

Bank Information Harvesting
The deVixor RAT uses multiple techniques to steal banking information. One of its main approaches involves collecting banking-related data from SMS messages. In addition, deVixor leverages a WebView injection technique to redirect victims to banking pages, where JavaScript-based injections are used to capture login credentials and other sensitive financial information.
SMS-Based Banking Data Harvesting
deVixor has implemented multiple commands to harvest banking information, including card details, bank balance amounts, SMSs coming from banks and crypto applications, and OTPs:
GET_BANK_BALANCE CommandThe command scans up to 5,000 SMS messages on the infected device to identify banking-related content, extract account balances and OTPs, and associate them with known Iranian banks using a hardcoded set of sender and bank keyword signatures.
It applies regular expressions to parse balances and OTP codes, checks whether the corresponding official banking applications are installed, and exfiltrates the results as a structured JSON response under the GET_ACCOUNT_SUMMARY command.
The report includes the bank name, balance, OTP availability and value, app installation status, and the total number of identified banks. (see Figure 7)

GET_CARD_NUMBER Command
Similar to the previous command, deVixor scans all SMS messages in the infected device’s inbox to identify credit and debit card numbers. It uses regular expressions to detect and validate card numbers, then exfiltrates the extracted information to the C&C server.
GET_EXCHANGE Command
This command scans the victim’s SMS inbox for messages originating from cryptocurrency exchanges and payment services. It extracts recent messages for each identified sender and exfiltrates the collected data to the C&C server. The malware specifically targets SMS messages associated with the following cryptocurrency exchanges (see Figure 8)
- Binance
- CoinEx
- Ramzinex
- Exir
- Tabdeal
- Bitbarg
- TetherLand
- AbanTether
- OkExchange
- ArzDigital
- IranCryptoMarket
- Cryptoland
- Bitex
- Excoino

GET_BANK_SMS Command
Similar to the GET_EXCHANGE command, this command collects the most recent SMS messages sent by known banks and payment services. The harvested messages are returned to the C&C server as a structured JSON response labeled GET_BANK_SMS. Below is the list of banks and payment services targeted by deVixor (see Figure 9)
- Bank Melli Iran
- Bank Mellat
- Bank Tejarat
- Bank Saderat Iran
- Bank Sepah
- Bank Maskan
- Bank Keshavarzi
- Bank Refah
- Bank Pasargad
- Bank Parsian
- Bank Ayandeh
- Bank Saman
- Bank Sina
- Bank Dey
- Post Bank Iran
- Middle East Bank
- Iran Zamin Bank
- Eghtesad Novin Bank
- Karafarin Bank
- Shahr Bank
- Hekmat Iranian Bank
- Industry & Mine Bank
- Export Development Bank of Iran
- Tavon Bank
- BluBank
- Iran Kish

This SMS-based financial information harvesting enables attackers to carry out banking fraud and account takeovers, leading to wallet draining and significant financial losses for victims.
Fake Bank Notification and Credential Harvesting
deVixor uses the “BankEntryNotification” command to generate fraudulent bank notifications designed to lure users into interacting with them. When a victim taps the notification, the malware loads a legitimate banking website inside a WebView and injects malicious JavaScript into the login forms.
Once the user enters their username and password and clicks the login button, the credentials are silently exfiltrated to the C&C server. The figure below illustrates the JavaScript injection technique used for credential harvesting. (see Figure 10)

Ransomware Activity
The deVixor RAT includes an embedded ransomware module that can be remotely triggered using the “RANSOMWARE” command. Upon receiving this command, the malware parses the attacker-supplied parameters, including the ransom note, a TRON cryptocurrency wallet address, and the demanded payment amount.
These details are stored locally in a file named LockTouch.json, which serves as a persistent configuration file to retain the ransomware state across device reboots. The malware then sets an internal locked status and prepares the ransom metadata used by the lock-screen component.
Based on screenshots shared on the threat actor’s Telegram channel, deVixor locks the victim’s device and displays a ransom message stating “Your device is locked. Deposit to unlock”, along with the attacker’s TRON wallet address and a demand of 50 TRX.
The malware also generates a response containing device identifiers and ransom-related details, which is sent back to the C&C server to track victim status and potential compliance. (see Figure 11)

This functionality demonstrates that deVixor is capable of conducting financial extortion, in addition to its existing capabilities for credential theft and user surveillance.
In addition to the features described above, the malware is capable of collecting all device notifications, capturing keystrokes, preventing uninstallation, hiding its presence, harvesting contacts, and taking screenshots. We’ve compiled a full list of supported commands below:
deVixor v1 and v2 Commands
| V1 Commands | V2 Commands | Description |
| RUN_USSD: | RUN_USSD: | Execute USSD request |
| SET_OF_MOD: | SEARCH_APP: | Finds the targeted application installed on the device |
| – | SEARCH_ALL_SMS | Search SMSs with the keywords, store the result in sms_search_keyword.txt, and send the file to the server. |
| BankEntryNotification: | BankEntryNotification: | Generate a fake Bank notification to initiate bank login activity and harvest credentials using JavaScript injection. |
| – | SET_WARNING_BANK: | Displays a fake bank security warning to trick users into logging in on fraudulent banking pages. |
| CHANGE_SERVER: | CHANGE_SERVER: | Change C&C server |
| CHANGE_FIREBASE: | CHANGE_FIREBASE: | Change the Firebase server |
| – | RANSOMWARE: | Initiate Ransomware Activity |
| SEND_SMS: | SEND_SMS: | Send SMS to the number received from the server |
| SEND_SMS_TO_ALL: | SEND_SMS_TO_ALL: | Send SMS to all the contacts saved in the infected device |
| GET_HISTORY_SMS: | GET_HISTORY_SMS: | Saves all SMSs from the infected device to chat_history_*.txt and sends it to the server |
| ADD_CONTACT: | ADD_CONTACT: | Insert the contact into the infected device’s contact list |
| IMPORT_VCF | IMPORT_VCF | Collects the vCard file |
| GET_CAMERA_PHOTOS | GET_CAMERA_PHOTOS | Collects pictures captured using the camera |
| – | GET_ALL_SENT_SMS | Collects sent sms history |
| – | NOTIFICATION_READER | Collect notifications |
| UNHIDE | UNHIDE | Appears again in the applications |
| SET_VIBRATE | SET_VIBRATE | SET_VIBRATION_MODE |
| – | BANK_WARNING | Collect the active fake bank warning list. |
| ONCHANGE | ONCHANGE | Disguise as a YouTube app |
| GET_APPS | GET_APPS | Collects the application package list |
| – | GET_GOLD | Collecting SMSs that are coming from the mentioned mobile numbers |
| SMS_TO_ALL | SMS_TO_ALL | Collects SIM information |
| GET_BANK_BALANCE | GET_BANK_BALANCE | Collects bank balance from SMSs |
| GET_BNC_APPS | GET_BNC_APPS | Collects the banking application list |
| – | GET_ALL_RECEIVED_SMS | Collects all received SMSs |
| GET_SIM_SMS | GET_SIM_SMS | Get SIM information |
| HIDE | HIDE | Hides application |
| TAKE_SCREENSHOT | TAKE_SCREENSHOT | Captures Screenshot |
| – | REMOVE_RANSOMWARE | Remove Ransomware Overlay |
| GET_DEVICE_INFO | GET_DEVICE_INFO | Collects device information |
| SET_SOUND | SET_SOUND | Set notification sound |
| OFFCHANGE | OFFCHANGE | Disable disguise and appear using the original app icon |
| GET_EXCHANGE | GET_EXCHANGE | Collect SMSs related to crypto exchange and financial services |
| GET_IPS | GET_IPS | Collect the IP address of the infected device |
| GET_CARD_NUMBER | GET_CARD_NUMBER | Collects card numbers from SMSs |
| GET_BANK_SMS | GET_BANK_SMS | Collecting all SMSs coming from banks |
| GET_ACCOUNT | GET_ACCOUNT | Get account details from the infected device |
| REVIVE_FOREGROUND | REVIVE_FOREGROUND | Sends the device’s active status |
| GET_USSD_INFO | GET_USSD_INFO | Get SIM Info to support USSD operations |
| GET_LAST_SMS | – | Collecting recent SMSs |
| GET_ALL_SMS | GET_ALL_SMS | Collect all SMSs |
| – | KEYLOGGER | Collects Keylogged data stored in file keuboard_history.txt |
| GET_SCREENSHOTS | GET_SCREENSHOTS | Collects screenshots from the server |
| GET_PHONE_NUMBER | GET_PHONE_NUMBER | Collect the device phone number |
| SET_SILENT | SET_SILENT | Put the device on silent |
| GET_GALLERY | GET_GALLERY | Collect gallery media |
| GET_CONTACTS | GET_CONTACTS | Collect contacts |
Conclusion
deVixor is a feature-rich Android banking Trojan that reflects the latest evolution of Android malware. It combines SMS-based financial data harvesting, WebView-based JavaScript injection attacks, ransomware capabilities, and full remote device control to facilitate banking fraud, account takeovers, financial extortion, and prolonged user surveillance from a single platform.
The modular command architecture, persistent configuration mechanisms, and an active development cycle all indicate that deVixor is not an isolated campaign, but a maintained and extensible criminal service.
The targeted focus on Iranian banks, payment services, and cryptocurrency platforms highlights deliberate victim profiling and regional specialization.
Cyble’s Threat Intelligence Platforms continuously monitor emerging threats, infrastructure, and activity across the dark web, deep web, and open sources. This proactive intelligence empowers organizations with early detection, impersonation, infrastructure mapping, and attribution insights. Altogether, these capabilities provide a critical head start in mitigating and responding to evolving cyber threats.
Our Recommendations
We have listed some essential cybersecurity best practices that create the first line of control against attackers. We recommend that our readers follow the best practices given below:
- Install Apps Only from Trusted Sources:
Download apps exclusively from official platforms, such as the Google Play Store. Avoid third-party app stores or links received via SMS, social media, or email. - Be Cautious with Permissions and Installs:
Never grant permissions and install an application unless you’re certain of an app’s legitimacy. - Watch for Phishing Pages:
Always verify the URL and avoid suspicious links and websites that ask for sensitive information. - Enable Multi-Factor Authentication (MFA):
Use MFA for banking and financial apps to add an extra layer of protection, even if credentials are compromised. - Report Suspicious Activity:
If you suspect you’ve been targeted or infected, report the incident to your bank and local authorities immediately. If necessary, reset your credentials and perform a factory reset. - Use Mobile Security Solutions:
Install a mobile security application that includes real-time scanning. - Keep Your Device Updated:
Ensure your Android OS and apps are updated regularly. Security patches often address vulnerabilities that malware exploits.
MITRE ATT&CK® Techniques
| Tactic | Technique ID | Procedure |
| Initial Access (TA0027) | Phishing (T1660) | Malware is distributed via a phishing site |
| Persistence (TA0028) | Event Triggered Execution: Broadcast Receivers(T1624.001) | deVixor registered the BOOT_COMPLETED broadcast receiver to activate on device startup |
| Persistence (TA0028) | Foreground Persistence (T1541) | deVixor uses foreground services by showing a notification |
| Defense Evasion (TA0030) | Hide Artifacts: Suppress Application Icon (T1628.001) | deVixor hides icon |
| Defense Evasion (TA0030) | Impair Defenses: Prevent Application Removal (T1629.001) | Prevent uninstallation |
| Defense Evasion (TA0030) | Impair Defenses: Disable or Modify Tools (T1629.003) | deVixor can disable Google Play Protect |
| Defense Evasion (TA0030) | Masquerading: Match Legitimate Name or Location (T1655.001) | Masquerade as a YouTube app |
| Defense Evasion (TA0030) | Obfuscated Files or Information (T1406) | deVixor uses an encrypted C&C server URL |
| Credential Access (TA0031) | Access Notifications (T1517) | deVixor collects device notifications |
| Credential Access (TA0031) | Input Capture: Keylogging (T1417.001) | deVixor collects keylogged data |
| Credential Access (TA0031) | Input Capture: GUI Input Capture (T1417.002) | deVixor collects entered banking credentials |
| Discovery (TA0032) | Software Discovery (T1418) | deVixor collects the installed application list |
| Discovery (TA0032) | System Information Discovery (T1426) | deVixor collects the device information |
| Collection (TA0035) | Archive Collected Data (T1532) | deVixor compressing collected data and saving to a .zip file |
| Collection (TA0035) | Data from Local System (T1533) | deVixor collects media from the gallery |
| Collection (TA0035) | Protected User Data: Contact List (T1636.003) | Collects contact data |
| Collection (TA0035) | Protected User Data: SMS Messages (T1636.004) | Collects SMS data |
| Collection (TA0035) | Protected User Data: Accounts (T1636.005) | deVixor collects Accounts data |
| Collection (TA0035) | Screen Capture (T1513) | deVixor can take Screenshots |
| Command and Control (TA0037) | Application Layer Protocol: Web Protocols (T1437.001) | Malware uses HTTPs protocol |
| Exfiltration (TA0036) | Exfiltration Over C2 Channel (T1646) | deVixor sends collected data to the C&C server |
| Impact (TA0034) | SMS Control (T1582) | deVixor can send SMSs from the infected device |
Indicators of Compromise (IOCs)
The IOCs have been added to this GitHub repository. Please review and integrate them into your Threat Intelligence feed to enhance protection and improve your overall security posture.
