Attackers are exploiting a critical-severity privilege escalation vulnerability (CVE-2025–8489) in the King Addons for Elementor plugin for WordPress, which lets them obtain administrative permissions during the registration process.
The threat activity started on October 31, just a day after the issue was publicly disclosed. So far, the Wordfence security scanner from Defiant, a company that provides security services for WordPress websites, has blocked more than 48,400 exploit attempts.
King Addons is a third-party add-on for Elementor, a popular visual page builder plugin for WordPress sites. It is used on roughly 10,000 websites, providing additional widgets, templates, and features.
CVE-2025–8489, discovered by researcher Peter Thaleikis, is a flaw in the plugin’s registration handler that allows anyone signing up to specify their user role on the website, including the administrator role, without enforcing any restrictions.
According to observations from Wordfence, attackers send a crafted ‘admin-ajax.php’ request specifying ‘user_role=administrator,’ to create rogue admin accounts on targeted sites.
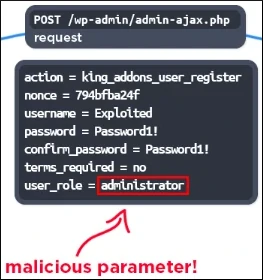
Source: Wordfence
The researchers noticed a peak in the exploitation activity between November 9 and 10, with two IP addresses being the most active: 45.61.157.120 (28,900 attempts) and 2602:fa59:3:424::1 (16,900 attempts).
Wordfence provides a more extensive list of offensive IP addresses and recommends that website administrators look for them in the log files. The presence of new administrator accounts is also a clear sign of compromise.
Website owners are advised to upgrade to version 51.1.35 of King Addons, which addresses CVE-2025–8489, released on September 25.
Wordfence researchers are also warning of another critical vulnerability in the Advanced Custom Fields: Extended plugin, active on more than 100,000 WordPress websites, which can be exploited by an unauthenticated attacker to execute code remotely.
The flaw affects versions 0.9.0.5 through 0.9.1.1 of the plugin and is currently tracked as CVE-2025-13486. It was discovered and reported responsibly by Marcin Dudek, the head of the national computer emergency response team (CERT) in Poland.
The vulnerability is “due to the function accepting user input and then passing that through call_user_func_array(),” Wordfence explains.
“This makes it possible for unauthenticated attackers to execute arbitrary code on the server, which can be leveraged to inject backdoors or create new administrative user accounts.”
The security issue was reported on November 18, and the plugin vendor addressed it in version 0.9.2 of Advanced Custom Fields: Extended, released a day after receiving the vulnerability report.
Given that the flaw can be leveraged without authentication only through a crafted request, the public disclosure of technical details is likely to generate malicious activity.
Website owners are advised to move to the latest version as soon as possible or disable the plugin on their sites.

Broken IAM isn’t just an IT problem – the impact ripples across your whole business.
This practical guide covers why traditional IAM practices fail to keep up with modern demands, examples of what “good” IAM looks like, and a simple checklist for building a scalable strategy.
