Table of Contents
When it comes to spotting threats, security teams need tools that can pull data from all over and make it easier to analyze. In this article, we’ll take a look at some popular open-source tools that help with everything from log management to network and host monitoring, and even incident response. These tools give teams the visibility they need to catch threats early and act fast.
Cortex
Cortex is developed by TheHive Project to help SOCs, CSIRTs, and security researchers analyze observables at scale from a single interface. It supports analysis of IP addresses, URLs, domain names, file hashes, and more, either individually or in bulk, via a web interface or REST API.
Cortex eliminates the need to manually integrate multiple tools by providing a centralized platform with built-in analyzers. Additional analyzers can be developed and shared across teams or the wider community, streamlining investigations and improving collaboration.

Fluentd
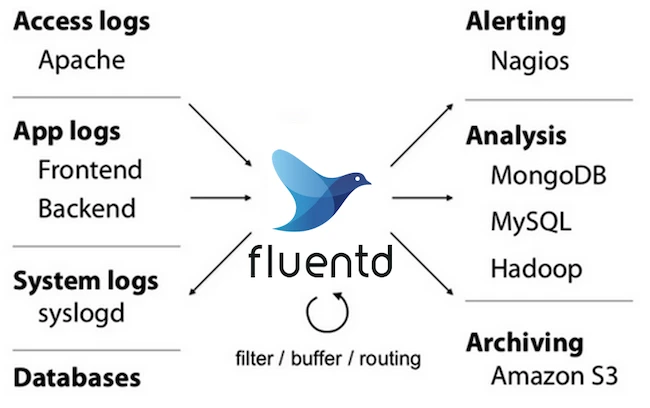
Fluentd is a data collector that unifies data collection and delivery, making data easier to process and understand.
Fluentd decouples data sources from backend systems by providing a unified logging layer. This enables real-time access to diverse log types while reducing the risk of bad data affecting performance or decision-making. By standardizing log collection, Fluentd helps organizations accelerate development.

Security Onion
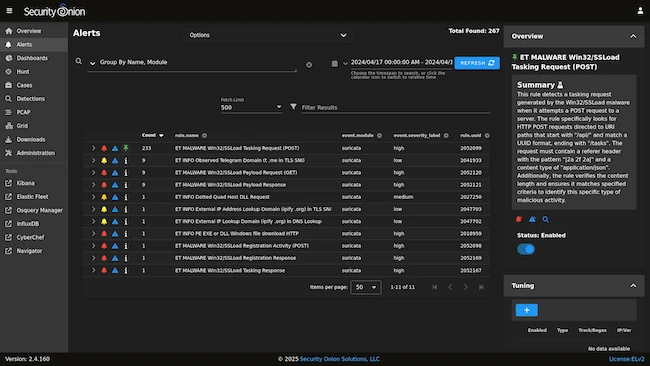
Security Onion provides network visibility, host visibility, intrusion detection honeypots, log management, and case management.
For network visibility, it supports signature-based detection with Suricata, protocol metadata and file extraction using Zeek or Suricata, packet capture with Stenographer or Suricata, and file analysis. Host visibility is handled through the Elastic Agent, which enables data collection, live queries with osquery, and centralized management via Elastic Fleet. OpenCanary-based intrusion detection honeypots can also be added to increase enterprise visibility.
All collected logs are sent to Elasticsearch. Custom user interfaces are provided for alerts, dashboards, threat hunting, case management, and grid management.

Snort
Snort is an Intrusion Prevention System (IPS). It uses a set of rules to detect suspicious network activity and alerts users when it finds a match.
Snort can also be configured to block malicious traffic in real time. It has three main functions: it can act as a packet sniffer like tcpdump, serve as a packet logger for analyzing network traffic, or operate as a complete intrusion prevention system.


Suricata
Suricata is a network intrusion detection system (IDS), intrusion prevention system (IPS), and network security monitoring engine.
Suricata offers capabilities for network security monitoring (NSM), including logging HTTP requests, capturing and storing TLS certificates, and extracting files from network flows for disk storage. Its support for packet capture (pcap) simplifies in-depth traffic analysis.

UTMStack
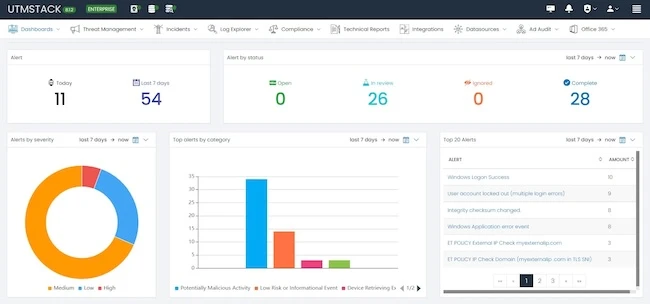
UTMStack is a unified threat management platform that combines Security Information and Event Management (SIEM) and Extended Detection and Response (XDR) technologies. It enables real-time correlation of log data, threat intelligence, and malware activity patterns from multiple sources to detect and stop threats.
The platform analyzes log data in real time to identify and neutralize threats at their origin, even if the threat isn’t directly detected on the affected server. Correlation occurs before data ingestion, reducing system workload and accelerating response times.

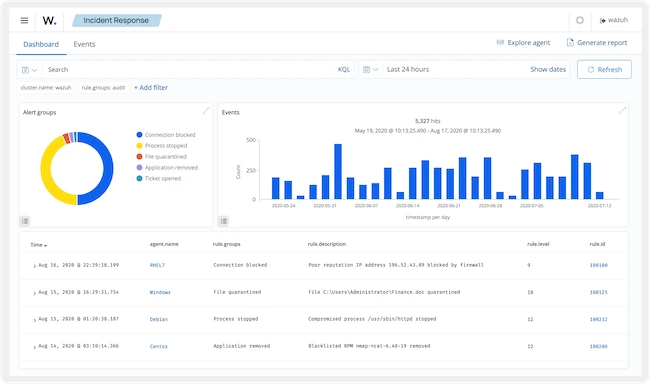
Wazuh
Wazuh is a security platform for threat prevention, detection, and response. It supports a wide range of environments, including on-premises, virtualized, containerized, and cloud-based systems.
Wazuh consists of a lightweight security agent installed on monitored systems and a central management server that collects and analyzes data. It integrates with the Elastic Stack, offering a search engine and data visualization tools for exploring security events.

Must read:

Subscribe to the Help Net Security ad-free monthly newsletter to stay informed on the essential open-source cybersecurity tools. Subscribe here!

